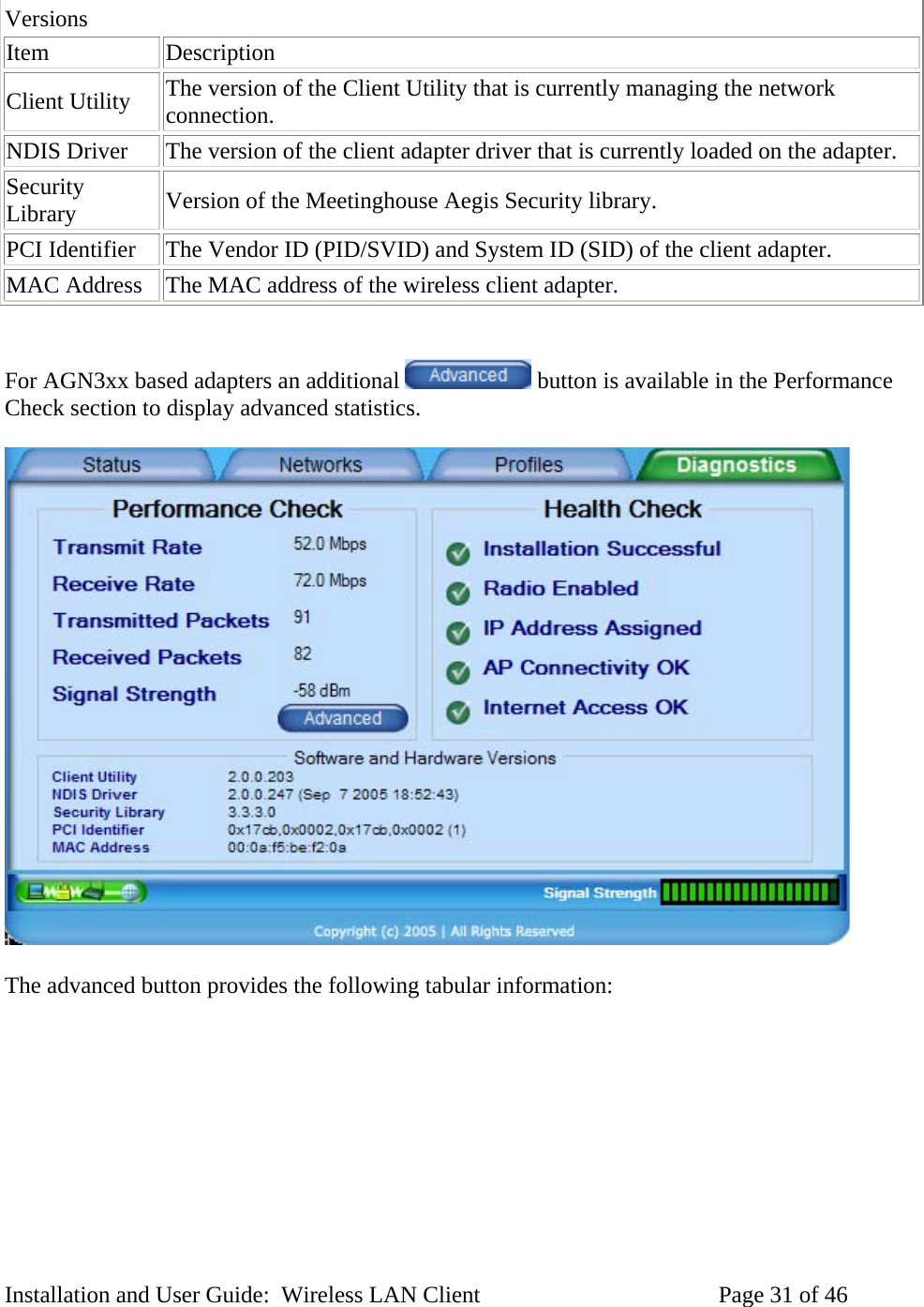
Airgo Networks AGN3022UB1100 Airgo 3000 Series USB Adapter 2X2 User Manual Installation and User Guide
Airgo Networks Inc. Airgo 3000 Series USB Adapter 2X2 Installation and User Guide
Contents
- 1. User Manual
- 2. USB module label RFx in User Manual
User Manual