Arcadyan Technology AR4505NW DIGITAL TRANSMISSION SYSTEM User Manual 3com
Arcadyan Technology Corporation DIGITAL TRANSMISSION SYSTEM 3com
Contents
- 1. USERS MANUAL 1 OF 4
- 2. USERS MANUAL 2 OF 4
- 3. USERS MANUAL 3 OF 4
- 4. USERS MANUAL 4 OF 4
USERS MANUAL 4 OF 4
Advanced 89
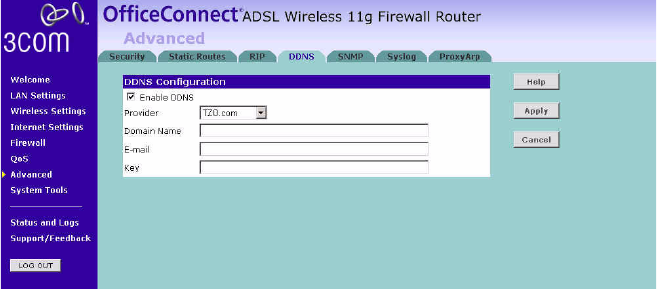
Before you set up DDNS, you must obtain an account, password or key
and static domain name from your DDNS provider.
DDNS is disabled by default.
Figure 74 Dynamic Domain Server (DDNS) Screen
1Check Enable DDNS.
2Select the provider, and then enter the necessary information provided by
your DDNS provider.
3Click Apply.
90 CHAPTER 5: CONFIGURING THE ROUTER
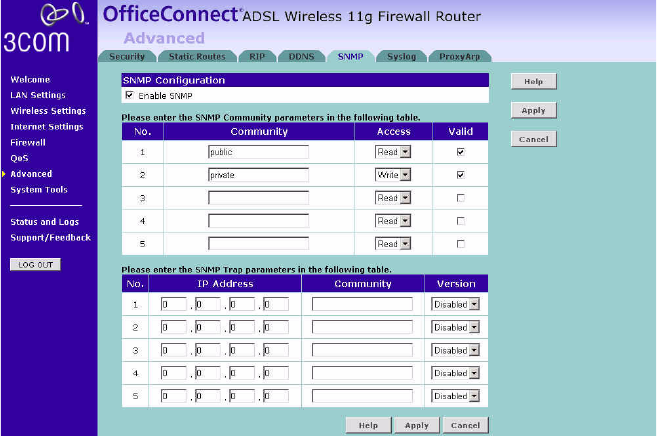
SNMP SNMP (Simple Network Management Protocol) allows remote
management of your router by a PC that has an SNMP management
agent installed.
Figure 75 SNMP Screen
To Configure SNMP Community:
1In the Community column, enter the name of the SNMP communication
channel. Your SNMP management agent needs to be configured with this
name so that it can communicate with your router.
2In the Access column, select Read to allow the management agent to
collect data (for example, bandwidth usage) from your router. Select
Write to allow the management agent to change the configuration of
your router.
3Check the appropriate Valid checkbox to enable the communication
channel.
Advanced 91
You can configure your router to send status messages to the SNMP
management agent if a problem occurs on the network. To configure
SNMP traps:
1In the IP Address field, enter the IP address of the PC to which you want
your router to send status messages.
2In the Community field, enter the name of the SNMP communication
channel to which you want your router to send status messages.
3Set the Version field to match the version of trap messaging that your
SNMP management agent supports. The router supports V1 and V2c trap
messaging.
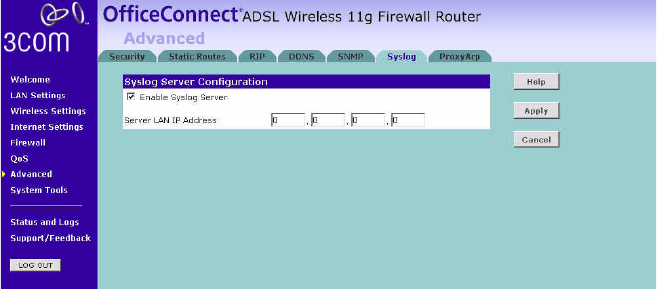
Syslog Using third party syslog software, this Syslog Server tool will automatically
download the Router log to the specified server IP address.
Figure 76 Syslog Server Screen
1Check the Enable Syslog Server checkbox.
2Enter the Server LAN IP Address in the space provided.
3Click Apply.
92 CHAPTER 5: CONFIGURING THE ROUTER
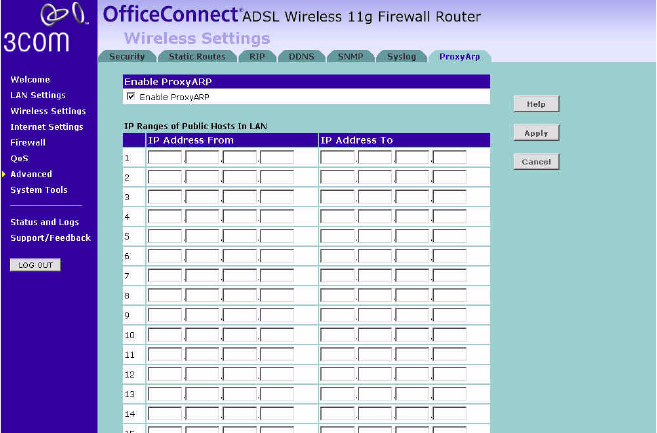
Proxy ARP Proxy ARP is the technique in which one host, usually a router, answers
ARP requests intended for another machine. By "faking" its identity, the
router accepts responsibility for routing packets to the "real" or intended
destination. This hightens the security for your network.
Figure 77 Proxy ARP Screen
Enter the corresponding IP address in the IP Address From and IP Address
To fields.
System Tools 93
System Tools These pages allows you to manage different parameters of the Router
and perform certain administrative functions.
Restart Router Sometimes it may be necessary to restart (or reboot) the Router.
Restarting the Router from this screen will not delete any of your
configuration settings.
Click the Restart the Router button to restart the Router.
Figure 78 Restart Router Screen
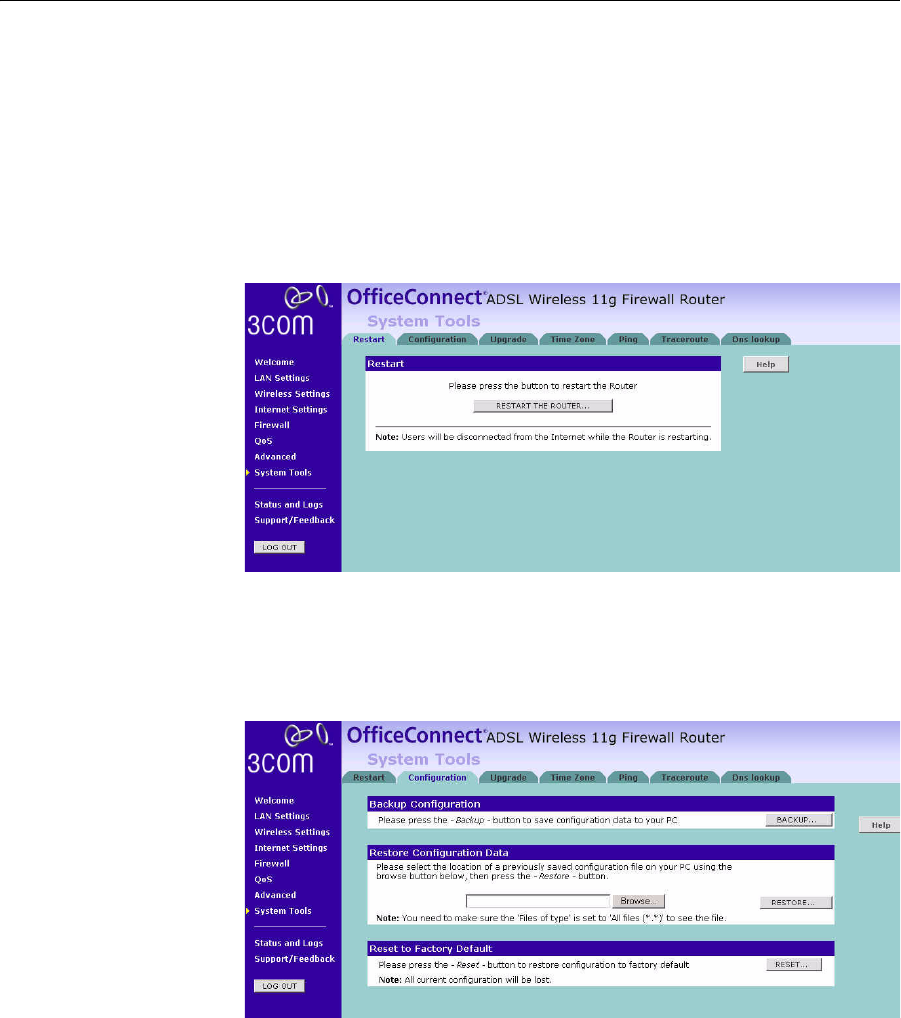
Configuration Use this configuration screen to backup, restore or reset the
configuration details of the Router.
Figure 79 Configuration Screen
94 CHAPTER 5: CONFIGURING THE ROUTER
■Backup Configuration — You can save your current configuration by
clicking the Backup button. Saving your configuration will allow you
to restore it later if your settings are lost or changed. It is
recommended that you backup your current configuration before
performing a firmware update.
■Restore Configuration Data — The Restore Settings option will allow
you to restore a previously saved configuration. Please select the
configuration file using the Browse button and click Restore.
■Reset to Factory Default — Using this option will reset all of the
settings in the Router to the factory default settings. It is
recommended that you backup your settings before you restore all of
the defaults. To restore the factory default settings, click Reset.
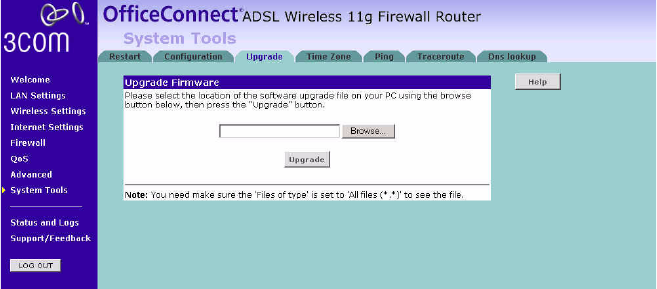
Upgrade From time to time 3Com may release new versions of the Router’s
firmware. Firmware updates contain improvements and fixes to problems
that may have existed.
Figure 80 Upgrade Screen
Please download the firmware file to your PC first, and then click Browse
and select the firmware file. Click Upgrade to upload the firmware to the
Router.
System Tools 95
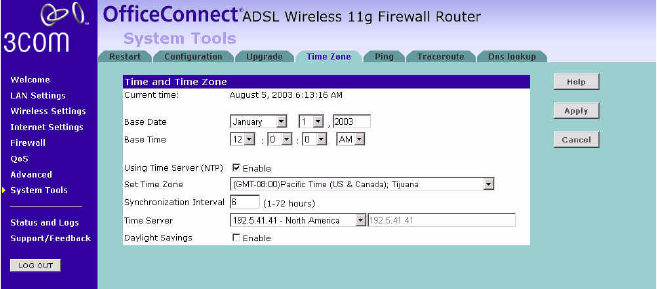
Time Zone You can set the time settings for the Router in this page.
Figure 81 Time Zone Screen
The Router keeps time by connecting to a Network Time Protocol (NTP)
server. This allows the Router to synchronize the system clock to the
Internet. The synchronized clock in the Router is used to record the
security log and control client filtering. Select the time zone that you
reside in. If you reside in an area that observes Daylight Saving, then
check the checkbox for Enable Daylight Saving. The system clock may not
update immediately. Allow at least 15 minutes for the router to contact
the time servers on the Internet and get a response. You cannot set the
clock yourself.
You can specify which NTP servers the Router will use to update the
system clock, although doing this should only be necessary if you are
experiencing difficulty.
96 CHAPTER 5: CONFIGURING THE ROUTER
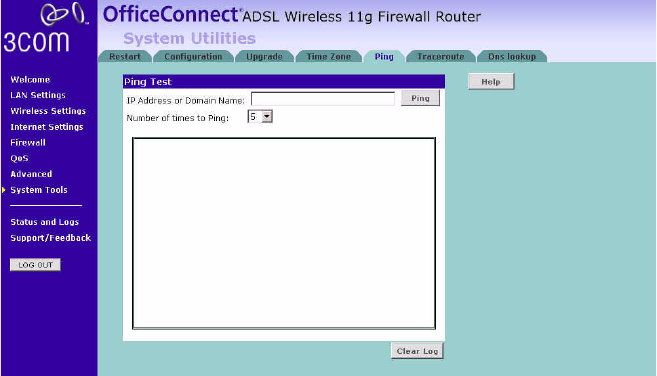
Ping The ping tool is used to test if the network is working properly.
Figure 82 Ping Screen
1Enter the IP address or domain name in the IP Address or Domain Name
field, and click Ping.
2Select from the Number of times to Ping drop-down menu.
3The Router keeps a log of the ping test, click Clear Log to delete the
records.
System Tools 97
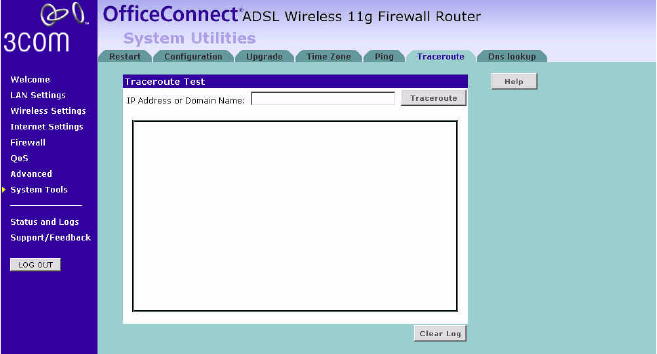
Traceroute Traceroute is the program that shows you the route over the network
between two systems, listing all the intermediate routers a connection
must pass through to get to its destination. It can help you determine
why your connections to a given server might be poor, and can often help
you figure out where exactly the problem is. It also shows you how
systems are connected to each other, letting you see how your ISP
connects to the Internet as well as how the target system is connected.
Figure 83 Traceroute Screen
1Enter the IP address or domain name in the IP Address or Domain Name
field, and click Traceroute.
2The Router keeps a log of the trace route test, click Clear Log to delete
the records.
98 CHAPTER 5: CONFIGURING THE ROUTER
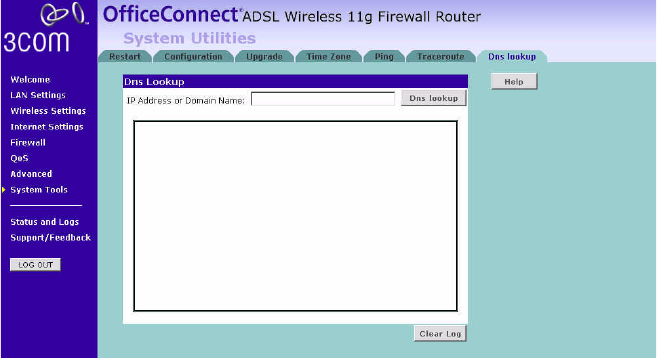
DNS Lookup DNS Lookup is the process of resolving an IP address
(i.e. 192.168.11.137) to a host name (i.e. xxxcompany.net).
Figure 84 DNS Lookup Screen
1Enter the IP address or domain name in the IP Address or Domain Name
field, and click Dns lookup.
2The Router keeps a log of the DNS lookup test, click Clear Log to delete
the records.
Status and Logs 99
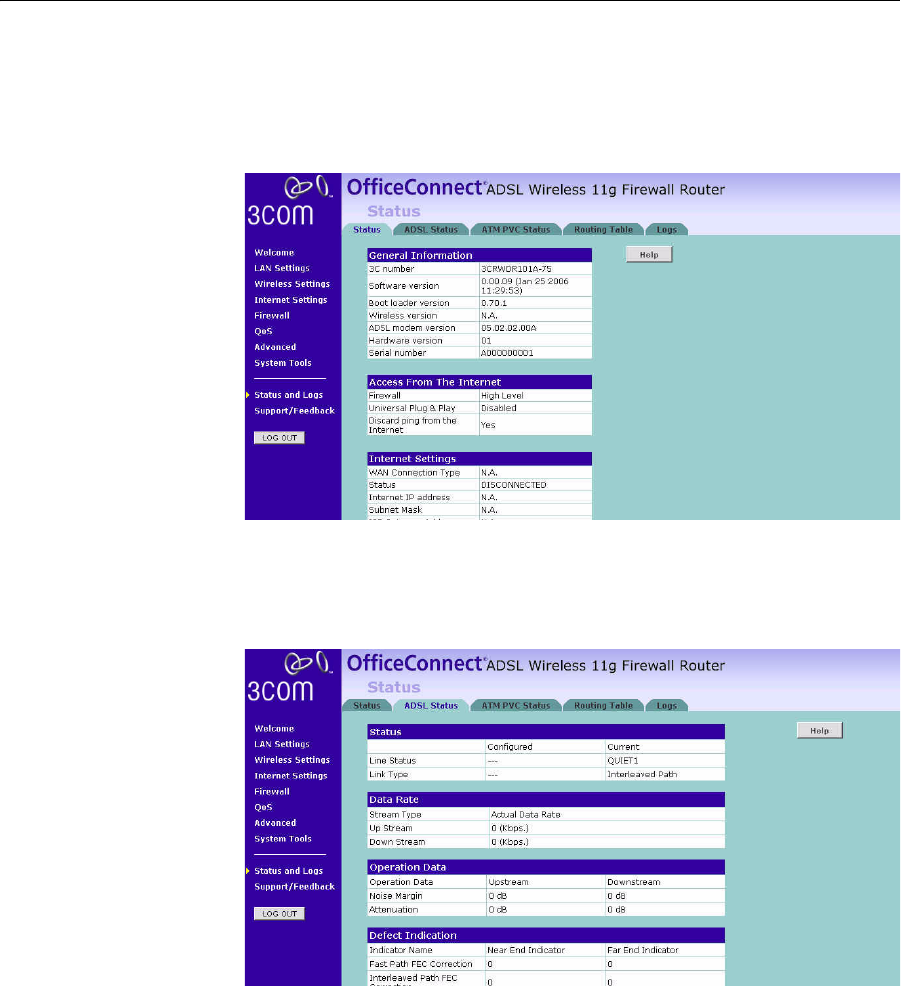
Status and Logs You can use the Status Screen to view version numbers for your Router’s
software and hardware and check the status of connections to WAN,
LAN and WLAN interfaces.
Status Figure 85 Status Screen
This screen shows Router status and statistics.
ADSL Status Figure 86 ADSL Status Screen
This screen shows ADSL modem status and statistics.
100 CHAPTER 5: CONFIGURING THE ROUTER
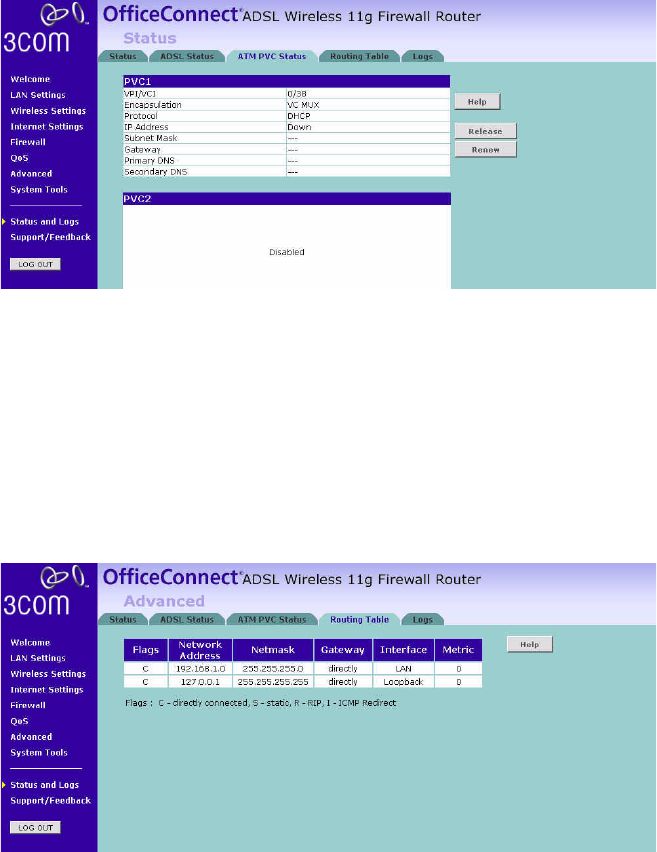
ATM PVC Status Figure 87 ATM PVC Status Screen
This screen shows ATM PVC status and statistics.
■Click Release to release the IP address from your ISP.
■Click Renew to obtain the IP address from your ISP.
Routing Table This screen displays details for the default routing used by your Router
and any routing created using Static Routing or RIP.
Figure 88 Routing Table Screen
Status and Logs 101
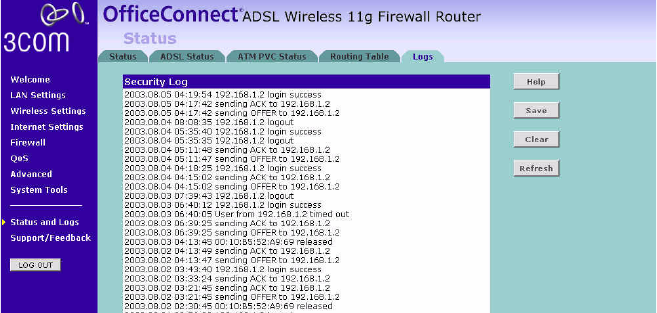
Logs This screen shows any attempts that have been made to gain access to
your network as well as the system activities.
Figure 89 Logs Screen
■Click Refresh to update the record.
■Click Clear to clear the log (note that all current entries will be erased).
■Click Save to save the log to the hard disk as a text file. When
prompted for a location to save the file to, specify a filename and
location, and then click OK.
102 CHAPTER 5: CONFIGURING THE ROUTER
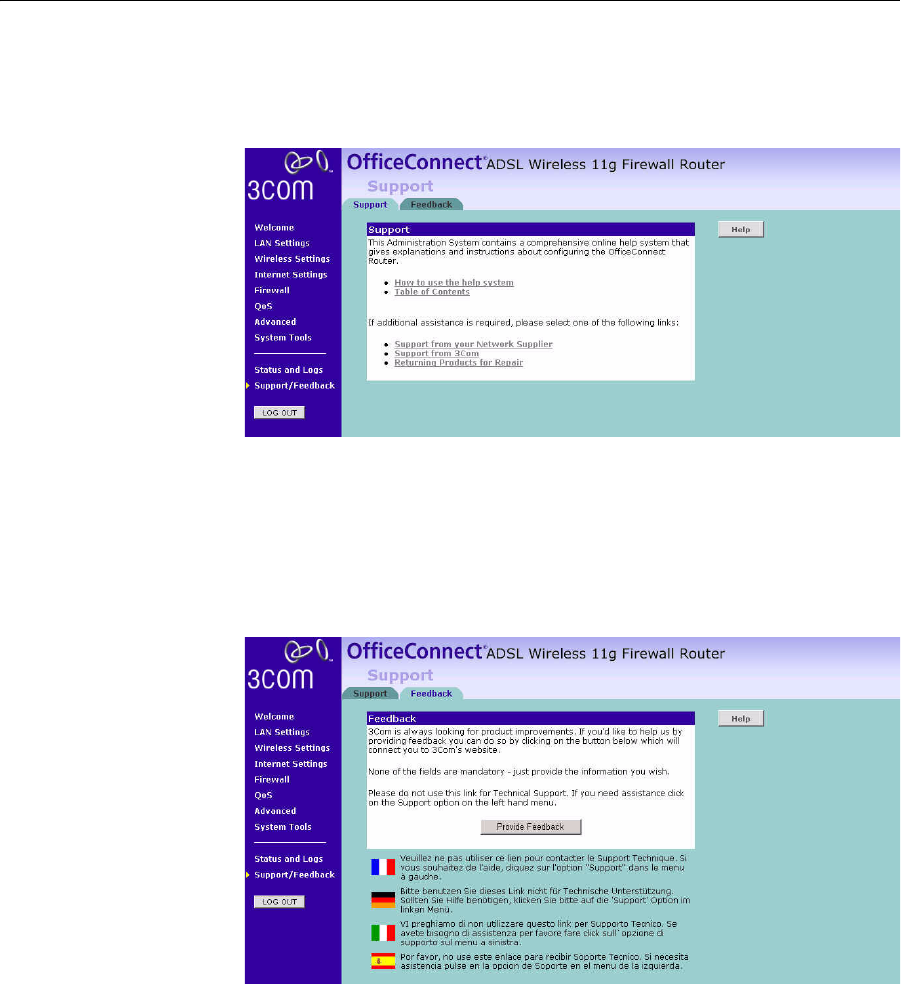
Support/Feedback You can use the Support/Feedback screen to obtain support and help,
and also provide feedback to 3Com.
Support Figure 90 Support Screen
This screen shows support information.
Feedback To provide feedback to 3Com, please click Provide Feedback, and this will
connect you to 3Com Web site.
Figure 91 Feedback Screen
This screen shows feedback information.

6TROUBLESHOOTING
Basic Connection
Checks
■Check that the Router is connected to your computers and to the
telephone line, and that all the equipment is powered on. Check that
the LAN Status and SYNC LEDs on the Router are illuminated, and that
any corresponding LEDs on the NIC are also illuminated.
■Ensure that the computers have completed their start-up procedure
and are ready for use. Some network interfaces may not be correctly
initialized until the start-up procedure has completed.
■If the link status LED does not illuminate for a port that is connected,
check that you do not have a faulty cable. Try a different cable.
Browsing to the
Router
Configuration
Screens
If you have connected your Router and computers together but cannot
browse to the Router configuration screens, check the following:
■Confirm that the physical connection between your computer and the
Router is OK, and that the LAN Status LEDs on the Router and
network adapter are illuminated and indicating the same speed
(10Mbps or 100Mbps). Some NICs do not have status LEDs, in which
case a diagnostic program may be available that can give you this
information.
■Ensure that you have configured your computer as described in
Chapter 3. Restart your computer while it is connected to the Router
to ensure that your computer receives an IP address.
■When entering the address of the Router into your web browser,
ensure that you use the full URL including the http:// prefix (e.g.
http://192.168.1.1).
■Ensure that you do not have a Web proxy enabled on your computer.
Go to the Control Panel and click on Internet Options. Select the
Connections tab and click on the LAN Settings button at the bottom.
Make sure that the Proxy Server option is unchecked.

104 CHAPTER 6: TROUBLESHOOTING
■If you cannot browse to the Router, use the winipcfg utility in
Windows 98/ME to verify that your computer has received the correct
address information from the Router. From the Start menu, choose
Run and then enter winipcfg. Check that the computer has an IP
address of the form 192.168.1.xxx (where xxx is in the range 2-254),
the subnet mask is 255.255.255.0, and the default Router is
192.168.1.1 (the address of the Router). If these are not correct, use
the Release and Renew functions to obtain a new IP address from the
Router. Under Windows 2000 and Windows XP, use the ipconfig
command-line utility to perform the same functions.
Connecting to the
Internet
If you can browse to the Router configuration screens but cannot access
web sites on the Internet, check the following:
■Confirm that the physical connection between the Router and the
telephone line is OK, and that the DSL LED on the Router is
illuminated.
■Ensure that you have entered the correct information into the Router
configuration screens as required by your Internet Service Provider. Use
the Internet Settings screen to verify this.
■Check that the PPPoE or PPPoA user name and password are correct.
■Ensure that your computers are not configured to use a Web proxy.
On Windows computers, this can be found under Control Panel >
Internet Options > Connections.
Forgotten Password
and Reset to
Factory Defaults
If you can browse to the Router configuration screen but cannot log on
because you do not know or have forgotten the password, follow the
steps below to reset the Router to its factory default configuration.
CAUTION: All your configuration changes will be lost, and you will need
to run the configuration wizard again before you can re-establish your
Router connection to the Internet. Also, other computer users will lose
their network connections whilst this process is taking place, so choose a
time when this would be convenient.
1Power off the Router.
2Disconnect all your computers and the telephone line from the Router.
3Re-apply power to the Router, and wait for it to finish booting up.

Wireless Networking 105
4Press and hold the Reset button on the rear panel (see “The rear panel
(Figure 4) of the Router contains four LAN ports, one ADSL port, a reset
button, a power switch, and a power adapter socket.” on page 15) for 5
seconds.
5The Router will restart, and when the start-up sequence has completed,
browse to:
http://192.168.1.1
and run the configuration wizard. You may need to restart your computer
before you attempt this.
6When the configuration wizard has completed, you may reconnect your
network as it was before.
Wireless
Networking
■Ensure that you have an 802.11b or 802.11g wireless adapter for
each wireless computer, and that it is correctly installed and
configured. Verify that each Wireless computer has either Windows
98 or higher or MAC OS 8.5 or higher.
■Verify that your wireless computers are configured to work in
Infrastructure mode and not Ad Hoc mode. The Router contains an
Access Point that is designed to operate in Infrastructure mode. Ad
Hoc mode is not supported by the Router.
■If you have a wired and a wireless NIC in the same computer, ensure
that the wired NIC is disabled.
■Check the status of the WLAN LED, it should be lit if wireless is
enabled and will flash when there is wireless activity. If not lit go to
“Wireless Settings” on page 43 and enable wireless networking.
■Ensure that the TCP/IP settings for all devices are correct.
■Ensure that the Wireless Clients are using the same SSID or Service
Area Name as the Router. The SSID is case-sensitive
■Ensure that the encryption method and level that you use on your
clients are the same as those configured on the Router. The Router
cannot simultaneously support WPA and WEP encryption.
■Ensure that you have the Wireless computer enabled in the list of
allowed MAC addresses if you are using MAC Address Filtering on the
Router.
■If you are having difficulty connecting or are operating at a low speed
try changing the antenna positions on the rear of the Router. For more
106 CHAPTER 6: TROUBLESHOOTING
effective coverage you can try reorientating your antennae. Place one
antenna vertically and one horizontally to improve coverage.
Additionally consider moving the wireless computer closer to the
Router to confirm that the building structure or fittings are not
adversely affecting the connectivity. If this resolves the problem
consider relocating the Wireless computer or the Router, or trying a
different channel on the Router.
■Sources of interference: The 2.4Ghz ISM band is used for 802.11b and
802.11g. This is generally a licence free band for low power
applications, and you may have other devices at your location that
operate in this frequency band. You should take care to ensure that
there are no devices like microwave ovens for example close to the
Router or wireless computers as this could affect receiver sensitivity
and reduce the performance of your network. If you are unsure try
relocating both the wireless computers and the Router to establish
whether this problem exists.
■Most wireless computer Adapters will scan the channels for the
wireless Router. If a wireless computer has not located the Router then
try initiating a search manually if the client software supports this
feature or manually set the channel on your wireless computer to
correspond to the Router channel number. Please refer to your
Wireless computer adapter documentation and vendor to do this.
■Speed of connection: The 802.11b and 802.11g standards will
automatically choose the best speed depending on the quality of your
connection. As the signal quality weakens then the speed falls back to
a lower speed. The speeds supported by 802.11g are 54 Mbps,
48 Mbps, 36 Mbps, 24 Mbps, 18 Mbps, 12 Mbps, and 6 Mbps. The
speeds supported by 802.11b are 11 Mbps, 5.5 Mbps, 2 Mbps and
1 Mbps. In general the closer you are to the Router the better the
speed. If you are not achieving the speed you had anticipated then try
moving the antenna on the Router or moving the Wireless computer
closer to the Router. In an ideal network the Router should be located
in the centre of the network with Wireless computers distributed
around it. Applications are generally available with the computer
wireless card to carry out a site survey. Use this application to find the
optimal siting for your wireless computer. Consult your Computer
Card documentation and vendor for more details.
Recovering from Corrupted Software 107
Recovering from
Corrupted Software
If the system software has become corrupted, the Router will enter a
“recovery” state; DHCP is enabled, and the LAN IP address is set to
192.168.1.1. Follow the instructions below to upload a new copy of the
system software to a Router unit in this state.
Ensure that one of your computers has a copy of the new software image
file stored on its hard disk or available on CD-ROM.
The latest software is available on 3Com’s Web site at:
www.3com.com
1Remove power from the Router and disconnect the telephone line and all
your computers, except for the one computer with the software image.
2You will need to reconfigure this computer to obtain an IP address
automatically (see “Obtaining an IP Address Automatically” on page 23)
3Restart the computer, and re-apply power to the Router.
4Using the Web browser on the computer, enter the following URL in the
location bar:
http://192.168.1.1.
This will connect you to the Recovery utility in the Router.
5Follow the on-screen instructions. Enter the path and filename of the
software image file.
6When the upload has completed, the Router will restart, run the self-test
and, if successful, resume normal operation.
7Refer to the Installation Guide to reconnect your Router to the telephone
line and the computers in your network. Do not forget to reconfigure the
computer you used for the software upload.
If the Router does not resume normal operation following the upload, it
may be faulty. Contact your supplier for advice.

108 CHAPTER 6: TROUBLESHOOTING
Frequently Asked
Questions
How do I reset the Router to Factory Defaults?
See “Forgotten Password and Reset to Factory Defaults” on
page 104.
How many computers on the LAN does the Router support?
A maximum of 253 computers on the LAN are supported.
How many wireless clients does the Router support?
A maximum of 128 wireless clients are supported.
There are only 4 LAN ports on the Router. How are additional
computers connected?
You can expand the number of connections available on your LAN
by using hubs, switches and wireless access points connected to
the Router. 3Com wireless access points and hubs and switches
provide a simple, reliable means of expanding your network;
contact your supplier for more information, or visit:
http://www.3com.com/
Does the Router support virtual private networks (VPNs)?
The Router supports VPN passthrough, which allows VPN clients on
the LAN to communicate with VPN hosts on the Internet. It is also
possible to set up VPN hosts on your LAN that clients elsewhere on
the Internet can connect to, but this is not a recommended
configuration.
Where can I download software updates for the Router?
Updates to the Router software are posted on the 3Com support
web site, accessible by visiting:
http://www.3com.com

AIP ADDRESSING
The Internet
Protocol Suite
The Internet protocol suite consists of a well-defined set of
communications protocols and several standard application protocols.
Transmission Control Protocol/Internet Protocol (TCP/IP) is probably the
most widely known and is a combination of two of the protocols (IP and
TCP) working together. TCP/IP is an internationally adopted and
supported networking standard that provides connectivity between
equipment from many vendors over a wide variety of networking
technologies.
Managing the
Router over the
Network
To manage a device over the network, the Router must be correctly
configured with the following IP information:
■An IP address
■A Subnet Mask
IP Addresses and
Subnet Masks
Each device on your network must have a unique IP address to operate
correctly. An IP address identifies the address of the device to which data
is being sent and the address of the destination network. IP addresses
have the format n.n.n.x where n is a decimal number between 0 and 255
and x is a number between 1 and 254 inclusive.
However, an IP Address alone is not enough to make your device operate.
In addition to the IP address, you need to set a subnet mask. All networks
are divided into smaller sub-networks and a subnet mask is a number
that enables a device to identify the sub-network to which it is
connected.

110 APPENDIX A: IP ADDRESSING
For your network to work correctly, all devices on the network must have:
■The same sub-network address.
■The same subnet mask.
The only value that will be different is the specific host device number.
This value must always be unique.
An example IP address is ‘192.168.100.8’. However, the size of the
network determines the structure of this IP Address. In using the Router,
you will probably only encounter two types of IP Address and subnet
mask structures.
Type One
In a small network, the IP address of ‘192.168.100.8’ is split into two
parts:
■Part one (‘192.168.100’) identifies the network on which the device
resides.
■Part two (‘.8’) identifies the device within the network.
This type of IP Address operates on a subnet mask of ‘255.255.255.0’.
See Table 3 for an example about how a network with three computers
and a Router might be configured.
Tabl e 3 IP Addressing and Subnet Masking
Type Two
In larger networks, where there are more devices, the IP address of
‘192.168.100.8’ is, again, split into two parts but is structured differently:
■Part one (‘192.168’) identifies the network on which the device
resides.
■Part two (‘.100.8’) identifies the device within the network.
Device IP Address Subnet Mask
PC 1 192.168.100.8 255.255.255.0
PC 2 192.168.100.33 255.255.255.0
PC 3 192.168.100.188 255.255.255.0
Router 192.168.100.72 255.255.255.0

How does a Device Obtain an IP Address and Subnet Mask? 111
This type of IP Address operates on a subnet mask of ‘255.255.0.0’.
See Table 4 for an example about how a network (only four computers
represented) and a Router might be configured.
Tabl e 4 IP Addressing and Subnet Masking
How does a Device
Obtain an IP
Address and Subnet
Mask?
There are three different ways to obtain an IP address and the subnet
mask. These are:
■Dynamic Host Configuration Protocol (DHCP) Addressing
■Static Addressing
■Automatic Addressing (Auto-IP Addressing)
DHCP Addressing The Router contains a DHCP server, which allows computers on your
network to obtain an IP address and subnet mask automatically. DHCP
assigns a temporary IP address and subnet mask which gets reallocated
once you disconnect from the network.
DHCP will work on any client Operating System such as Windows® 95,
Windows 98 or Windows NT 4.0. Also, using DHCP means that the same
IP address and subnet mask will never be duplicated for devices on the
network. DHCP is particularly useful for networks with large numbers of
users on them.
Static Addressing You must enter an IP Address and the subnet mask manually on every
device. Using a static IP and subnet mask means the address is
permanently fixed.
Auto-IP Addressing Network devices use automatic IP addressing if they are configured to
acquire an address using DHCP but are unable to contact a DHCP server.
Automatic IP addressing is a scheme where devices allocate themselves
Device IP Address Subnet Mask
PC 1 192.168.100.8 255.255.0.0
PC 2 192.168.201.30 255.255.0.0
PC 3 192.168.113.155 255.255.0.0
PC 4 192.168.002.230 255.255.0.0
Router 192.168.002.72 255.255.0.0
112 APPENDIX A: IP ADDRESSING
an IP address at random from the industry standard subnet of
169.254.x.x (with a subnet mask of 255.255.0.0). If two devices allocate
themselves the same address, the conflict is detected and one of the
devices allocates itself a new address.
Automatic IP addressing support was introduced by Microsoft in the
Windows 98 operating system and is also supported in Windows 2000.

BTECHNICAL SPECIFICATIONS
This section lists the technical specifications for the OfficeConnect ADSL
Wireless 11g Firewall Router.
OfficeConnect ADSL
Wireless 11g
Firewall Router
Interfaces
DSL connection
LAN connection — four 10Mbps/100Mbps dual speed Ethernet ports
(10BASE-T/100BASE-TX)
WLAN Interfaces
Standard IEEE 802.11g, Direct Sequence Spread Spectrum (DSSS)
Transmission rate: 54Mbps, automatic fallback to 48, 36, 24, 18, 12, or
6Mbps
Maximum channels: 13
Range up to 304.8m (1000ft)
Operating Channel and Frequency:
USA - FCC
2412~2462MHz (Ch1~Ch11)
Canada - IC
2412~2462MHz (Ch1~Ch11)
Europe - ETSI
2412~2472MHz (Ch1~Ch13)
Spain
2457~2462MHz (Ch10~Ch11)
France
2457~2472MHz (Ch10~Ch13)
Japan - STD-T66/STD-33
2412~2484MHz (Ch1~Ch14)
Sensitivity: 6, 12, 18, 24, 36, 48 Mbps: -85 dBm;
54 Mbps -66 dBm typical
Modulation: CCK, BPSK, QPSK, OFDM
114 APPENDIX B: TECHNICAL SPECIFICATIONS
Encryption: 40/64 bit WEP, 128 bit WEP, WPA
Maximum clients: 128
O/P Power: 18dBm
Standard IEEE 802.11b, Direct Sequence Spread Spectrum (DSSS)
Transmission rate: 11bps, automatic fallback to 5.5, 2, or 1 Mbps
Maximum channels: 13
Range up to 304.8m (1000ft)
Operating Channel and Frequency:
USA - FCC
2412~2462MHz (Ch1~Ch11)
Canada - IC
2412~2462MHz (Ch1~Ch11)
Europe - ETSI
2412~2472MHz (Ch1~Ch13)
Spain
2457~2462MHz (Ch10~Ch11)
France
2457~2472MHz (Ch10~Ch13)
Japan - STD-T66/STD-33
2412~2484MHz (Ch1~Ch14)
Sensitivity: 1, 2, 5.5 Mbps: -85 dBm; 11 Mbps -82 dBm typical
Modulation: CCK, BPSK, QPSK
Encryption: 40/64 bit WEP, 128 bit WEP, WPA
Maximum clients: 128
O/P Power 16dBm
Operating Temperature
0 °C to 40 °C (32 °F to 105 °F)
Power
8VA, 25 BThU/hr
Humidity
0% to 90% (non-condensing) humidity
Dimensions
■Width = 220 mm (8.7 in.)
■Depth = 133 mm (5.2 in.)
■Height = 38 mm (1.5 in.)

OfficeConnect ADSL Wireless 11g Firewall Router 115
Weight
Approximately 550 g (1.1 lbs)
Standards Functional: ISO 8802/3
IEEE 802.3
IEEE 802.11b, 802.11g
Safety: EN 60950
EMC: EN 55022 Class B
EN 55024
FCC Part 15 Class B*
ETSI EN 301 489–17
Radio ETS 300 328 (2.4 GHz ISM band wide band transmission
systems.
Environmental: EN 60068 (IEC 68)
*See “Regulatory Notices” for conditions of operation.
System Requirements Operating Systems
The Router will support the following Operating Systems:
■Windows 98Se
■Windows NT 4.0
■Windows ME
■Windows 2000
■Windows XP
■Mac OS 8.5 or higher
■Unix
Ethernet Performance The Router complies to the IEEE 802.3i, u and x specifications.
116 APPENDIX B: TECHNICAL SPECIFICATIONS
Cable Specifications The Router supports the following cable types and maximum lengths:
■Category 3 (Ethernet) or Category 5 (Fast Ethernet or Dual Speed
Ethernet) Twisted Pair — shielded and unshielded cable types.
■Maximum cable length of 100m (327.86 ft).

CSAFETY INFORMATION
Important Safety
Information
WARNING: Warnings contain directions that you must follow for your
personal safety. Follow all directions carefully.
You must read the following safety information carefully before you
install or remove the unit:
WARNING: The Router generates and uses radio frequency (rf) energy. In
some environments, the use of rf energy is not permitted. The user
should seek local advice on whether or not rf energy is permitted within
the area of intended use.
WARNING: Exceptional care must be taken during installation and
removal of the unit.
WARNING: To ensure compliance with international safety standards,
only use the power adapter that is supplied with the unit.
WARNING: The socket outlet must be near to the unit and easily
accessible. You can only remove power from the unit by disconnecting
the power cord from the outlet.
WARNING: This unit operates under SELV (Safety Extra Low Voltage)
conditions according to IEC 60950. The conditions are only maintained
if the equipment to which it is connected also operates under SELV
conditions.
WARNING: There are no user-replaceable fuses or user-serviceable
parts inside the Router. If you have a physical problem with the unit
that cannot be solved with problem solving actions in this guide,
contact your supplier.
WARNING: Disconnect the power adapter before moving the unit.

118 APPENDIX C: SAFETY INFORMATION
WARNING: RJ-45 ports. These are shielded RJ-45 data sockets. They
cannot be used as telephone sockets. Only connect RJ-45 data
connectors to these sockets.
Wichtige
Sicherheitshinweise
VORSICHT: Warnhinweise enthalten Anweisungen, die Sie zu Ihrer
eigenen Sicherheit befolgen müssen. Alle Anweisungen sind sorgfältig
zu befolgen.
Sie müssen die folgenden Sicherheitsinformationen sorgfältig
durchlesen, bevor Sie das Geräts installieren oder ausbauen:
VORSICHT: Der Router erzeugt und verwendet Funkfrequenz (RF). In
manchen Umgebungen ist die Verwendung von Funkfrequenz nicht
gestattet. Erkundigen Sie sich bei den zuständigen Stellen, ob die
Verwendung von Funkfrequenz in dem Bereich, in dem der Bluetooth
Access Point eingesetzt werden soll, erlaubt ist.
VORSICHT: Bei der Installation und beim Ausbau des Geräts ist mit
höchster Vorsicht vorzugehen.
VORSICHT: Aufgrund von internationalen Sicherheitsnormen darf das
Gerät nur mit dem mitgelieferten Netzadapter verwendet werden.
VORSICHT: Die Netzsteckdose muß in der Nähe des Geräts und leicht
zugänglich sein. Die Stromversorgung des Geräts kann nur durch
Herausziehen des Gerätenetzkabels aus der Netzsteckdose
unterbrochen werden.
VORSICHT: Der Betrieb dieses Geräts erfolgt unter den
SELV-Bedingungen (Sicherheitskleinstspannung) gemäß IEC 60950.
Diese Bedingungen sind nur gegeben, wenn auch die an das Gerät
angeschlossenen Geräte unter SELV-Bedingungen betrieben werden.

119
VORSICHT: Es sind keine von dem Benutzer zu ersetzende oder zu
wartende Teile in dem Gerät vorhanden. Wenn Sie ein Problem mit
dem Router haben, das nicht mittels der Fehleranalyse in dieser
Anleitung behoben werden kann, setzen Sie sich mit Ihrem Lieferanten
in Verbindung.
VORSICHT: Vor dem Ausbau des Geräts das Netzadapterkabel
herausziehen.
VORSICHT: RJ-45-Anschlüsse. Dies sind abgeschirmte
RJ-45-Datenbuchsen. Sie können nicht als Telefonanschlußbuchsen
verwendet werden. An diesen Buchsen dürfen nur RJ-45-Datenstecker
angeschlossen werden.
Consignes
importantes de
sécurité AVERTISSEMENT: Les avertissements présentent des consignes que
vous devez respecter pour garantir votre sécurité personnelle. Vous
devez respecter attentivement toutes les consignes.
Nous vous demandons de lire attentivement les consignes suivantes de
sécurité avant d’installer ou de retirer l’appareil:
AVERTISSEMENT: La Router fournit et utilise de l'énergie
radioélectrique (radio fréquence -rf). L'utilisation de l'énergie
radioélectrique est interdite dans certains environnements. L'utilisateur
devra se renseigner sur l'autorisation de cette énergie dans la zone
prévue.
AVERTISSEMENT: Faites très attention lors de l'installation et de la
dépose du groupe.
AVERTISSEMENT: Pour garantir le respect des normes internationales
de sécurité, utilisez uniquement l'adaptateur électrique remis avec cet
appareil.
AVERTISSEMENT: La prise secteur doit se trouver à proximité de
l’appareil et son accès doit être facile. Vous ne pouvez mettre l’appareil
hors circuit qu'en débranchant son cordon électrique au niveau de
cette prise.
AVERTISSEMENT: L’appareil fonctionne à une tension extrêmement
basse de sécurité qui est conforme à la norme CEI 60950. Ces

120 APPENDIX C: SAFETY INFORMATION
conditions ne sont maintenues que si l'équipement auquel il est
raccordé fonctionne dans les mêmes conditions.
AVERTISSEMENT: Il n’y a pas de parties remplaceables par les
utilisateurs ou entretenues par les utilisateurs à l’intérieur du moyeu. Si
vous avez un problème physique avec le moyeu qui ne peut pas être
résolu avec les actions de la résolution des problèmes dans ce guide,
contacter votre fournisseur.
AVERTISSEMENT: Débranchez l'adaptateur électrique avant de retirer
cet appareil.
AVERTISSEMENT: Ports RJ-45. Il s'agit de prises femelles blindées de
données RJ-45. Vous ne pouvez pas les utiliser comme prise de
téléphone. Branchez uniquement des connecteurs de données RJ-45 sur
ces prises femelles.

DEND USER SOFTWARE LICENSE
AGREEMENT
3Com Corporation
END USER SOFTWARE LICENSE AGREEMENT
YOU SHOULD CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS BEFORE DOWNLOADING, INSTALLING AND USING THIS
PRODUCT, THE USE OF WHICH IS LICENSED BY 3COM CORPORATION ("3COM") TO ITS CUSTOMERS FOR THEIR USE ONLY AS SET FORTH
BELOW. DOWNLOADING, INSTALLING OR OTHERWISE USING ANY PART OF THE SOFTWARE OR DOCUMENTATION INDICATES THAT YOU
ACCEPT THESE TERMS AND CONDITIONS. IF YOU DO NOT AGREE TO THE TERMS AND CONDITIONS OF THIS AGREEMENT, DO NOT
DOWNLOAD, INSTALL OR OTHERWISE USE THE SOFTWARE OR DOCUMENTATION, DO NOT CLICK ON THE "I AGREE" OR SIMILAR BUTTON.
AND IF YOU HAVE RECEIVED THE SOFTWARE AND DOCUMENTATION ON PHYSICAL MEDIA, RETURN THE ENTIRE PRODUCT WITH THE
SOFTWARE AND DOCUMENTATION UNUSED TO THE SUPPLIER WHERE YOU OBTAINED IT.
LICENSE: 3Com grants you a nonexclusive, nontransferable (except as specified herein) license to use the accompanying software program(s) in
executable form (the "Software") and accompanying documentation (the "Documentation"), subject to the terms and restrictions set forth in this
Agreement. You are not permitted to lease, rent, distribute or sublicense (except as specified herein) the Software or Documentation or to use the
Software or Documentation in a time-sharing arrangement or in any other unauthorized manner. Further, no license is granted to you in the human
readable code of the Software (source code). Except as provided below, this Agreement does not grant you any rights to patents, copyrights, trade
secrets, trademarks, or any other rights with respect to the Software or Documentation.
Subject to the restrictions set forth herein, the Software is licensed to be used on any workstation or any network server owned by or leased to you, for
your internal use, provided that the Software is used only in connection with this 3Com product. You may reproduce and provide one (1) copy of the
Software and Documentation for each such workstation or network server on which the Software is used as permitted hereunder. Otherwise, the
Software and Documentation may be copied only as essential for backup or archive purposes in support of your use of the Software as permitted
hereunder. Each copy of the Software and Documentation must contain 3Com's and its licensors' proprietary rights and copyright notices in the same
form as on the original. You agree not to remove or deface any portion of any legend provided on any licensed program or documentation delivered to
you under this Agreement.
ASSIGNMENT; NO REVERSE ENGINEERING: You may transfer the Software, Documentation and the licenses granted herein to another party in the
same country in which you obtained the Software and Documentation if the other party agrees in writing to accept and be bound by the terms and
conditions of this Agreement. If you transfer the Software and Documentation, you must at the same time either transfer all copies of the Software and
Documentation to the party or you must destroy any copies not transferred. Except as set forth above, you may not assign or transfer your rights under
this Agreement.
Modification, reverse engineering, reverse compiling, or disassembly of the Software is expressly prohibited. However, if you are a European Union
("EU") resident, information necessary to achieve interoperability of the Software with other programs within the meaning of the EU Directive on the
Legal Protection of Computer Programs is available to you from 3Com upon written request.
EXPORT RESTRICTIONS: The Software, including the Documentation and all related technical data (and any copies thereof) (collectively "Technical
Data"), is subject to United States Export control laws and may be subject to export or import regulations in other countries. In addition, the Technical
Data covered by this Agreement may contain data encryption code which is unlawful to export or transfer from the United States or country where you
legally obtained it without an approved U.S. Department of Commerce export license and appropriate foreign export or import license, as required. You
agree that you will not export or re-export the Technical Data (or any copies thereof) or any products utilizing the Technical Data in violation of any
applicable laws or regulations of the United States or the country where you legally obtained it. You are responsible for obtaining any licenses to export,
re-export or import the Technical Data.
In addition to the above, the Product may not be used, exported or re-exported (i) into or to a national or resident of any country to which the U.S. has
embargoed; or (ii) to any one on the U.S. Commerce Department's Table of Denial Orders or the U.S. Treasury Department's list of Specially Designated
Nationals.
TRADE SECRETS; TITLE: You acknowledge and agree that the structure, sequence and organization of the Software are the valuable trade secrets of
3Com and its suppliers. You agree to hold such trade secrets in confidence. You further acknowledge and agree that ownership of, and title to, the
Software and Documentation and all subsequent copies thereof regardless of the form or media are held by 3Com and its suppliers.
UNITED STATES GOVERNMENT LEGENDS: The Software, Documentation and any other technical data provided hereunder is commercial in nature
122 APPENDIX D: END USER SOFTWARE LICENSE AGREEMENT
and developed solely at private expense. The Software is delivered as "Commercial Computer Software" as defined in DFARS 252.227-7014 (June
1995) or as a commercial item as defined in FAR 2.101(a) and as such is provided with only such rights as are provided in this Agreement, which is
3Com's standard commercial license for the Software. Technical data is provided with limited rights only as provided in DFAR 252.227-7015 (Nov.
1995) or FAR 52.227-14 (June 1987), whichever is applicable.
TERM AND TERMINATION: The licenses granted hereunder are perpetual unless terminated earlier as specified below. You may terminate the licenses
and this Agreement at any time by destroying the Software and Documentation together with all copies and merged portions in any form. The licenses
and this Agreement will also terminate immediately if you fail to comply with any term or condition of this Agreement. Upon such termination you
agree to destroy the Software and Documentation, together with all copies and merged portions in any form.
LIMITED WARRANTIES AND LIMITATION OF LIABILITY: All warranties and limitations of liability applicable to the Software are as stated on the
Limited Warranty Card or in the product manual, whether in paper or electronic form, accompanying the Software. Such warranties and limitations of
liability are incorporated herein in their entirety by this reference.
GOVERNING LAW: This Agreement shall be governed by the laws of the State of California, U.S.A. excluding its conflicts of laws principles and
excluding the United Nations Convention on Contracts for the International Sale of Goods.
SEVERABILITY: In the event any provision of this Agreement is found to be invalid, illegal or unenforceable, the validity, legality and enforceability of
any of the remaining provisions shall not in any way be affected or impaired and a valid, legal and enforceable provision of similar intent and economic
impact shall be substituted therefor.
ENTIRE AGREEMENT: This Agreement sets forth the entire understanding and agreement between you and 3Com and supersedes all prior
agreements, whether written or oral, with respect to the Software and Documentation, and may be amended only in a writing signed by both parties.
Should you have any questions concerning this Agreement or if you desire to contact 3Com for any reason, please contact the 3Com subsidiary serving
your country, or write:
3Com Corporation, 350 Campus Drive, Marlborough, MA. USA 01752-3064

DOBTAINING SUPPORT FOR YOUR
PRODUCT
Register Your
Product
Warranty and other service benefits start from the date of purchase, so it
is important to register your product quickly to ensure you get full use of
the warranty and other service benefits available to you.
Warranty and other service benefits are enabled through product
registration. Register your product at http://eSupport.3com.com/.
3Com eSupport services are based on accounts that you create or have
authorization to access. First time users must apply for a user name and
password that provides access to a number of eSupport features
including Product Registration, Repair Services, and Service Request. If
you have trouble registering your product, please contact 3Com Global
Services for assistance.
Purchase
Value-Added
Services
To enhance response times or extend warranty benefits, contact 3Com or
your authorized 3Com reseller. Value-added services like 3Com ExpressSM
and GuardianSM can include 24x7 telephone technical support, software
upgrades, onsite assistance or advance hardware replacement.
Experienced engineers are available to manage your installation with
minimal disruption to your network. Expert assessment and
implementation services are offered to fill resource gaps and ensure the
success of your networking projects. More information on 3Com
maintenance and Professional Services is available at www.3com.com.
Contact your authorized 3Com reseller or 3Com for a complete list of the
value-added services available in your area.

124 APPENDIX D: OBTAINING SUPPORT FOR YOUR PRODUCT
Troubleshoot
Online
You will find support tools posted on the 3Com Web site at
www.3com.com.
3Com Knowledgebase helps you troubleshoot 3Com products. This
query-based interactive tool is located at
http://knowledgebase.3com.com and contains thousands of technical
solutions written by 3Com support engineers.
Access Software
Downloads
Software Updates are the bug fix/maintenance releases for the version
of software initially purchased with the product. In order to access these
Software Updates you must first register your product on the 3Com Web
site at http://eSupport.3com.com/
First time users will need to apply for a user name and password. A link to
software downloads can be found at http://eSupport.3com.com/, or
under the Product Support heading at www.3com.com.
Software Upgrades are the feature releases that follow the software
version included with your original product. In order to access upgrades
and related documentation you must first purchase a service contract
from 3Com or your reseller.
Telephone Technical
Support and Repair
To enable telephone support and other service benefits, you must first
register your product at http://eSupport.3com.com/
Warranty and other service benefits start from the date of purchase, so it
is important to register your product quickly to ensure you get full use of
the warranty and other service benefits available to you.
When you contact 3Com for assistance, please have the following
information ready:
■Product model name, part number, and serial number
■Proof of purchase, if you have not pre-registered your product
■A list of system hardware and software, including revision level
■Diagnostic error messages
■Details about recent configuration changes, if applicable

Contact Us 125
To send a product directly to 3Com for repair, you must first obtain a
return authorization number (RMA). Products sent to 3Com, without
authorization numbers clearly marked on the outside of the package, will
be returned to the sender unopened, at the sender’s expense. If your
product is registered and under warranty, you can obtain an RMA
number online at http://eSupport.3com.com/. First time users will
need to apply for a user name and password.
Contact Us 3Com offers telephone, e-mail and internet access to technical support
and repair services. To access these services for your region, use the
appropriate telephone number, URL or e-mail address from the list below.
Telephone numbers are correct at the time of publication. Find a current
directory of contact information posted on the 3Com Web site at
http://csoweb4.3com.com/contactus/
Country Telephone Number Country Telephone Number
Asia, Pacific Rim Telephone Technical Support and Repair
Australia
Hong Kong
India
Indonesia
Japan
Malaysia
New Zealand
Pakistan
1 800 678 515
800 933 486
+61 2 9424 5179 or
000800 650 1111
001 803 61009
00531 616 439 or
03 3507 5984
1800 801 777
0800 446 398
+61 2 9937 5083
Philippines
P. R . o f C h i n a
Singapore
S. Korea
Taiwan
Thailand
1235 61 266 2602 or
1800 1 888 9469
800 810 3033
800 6161 463
080 333 3308
00801 611 261
001 800 611 2000
You can also obtain support in this region using the following e-mail: apr_technical_support@3com.com
Or request a repair authorization number (RMA) by fax using this number: + 65 543 6348
Europe, Middle East, and Africa Telephone Technical Support and Repair
From anywhere in these
regions, call: +44 (0)1442 435529
From the following countries, you may use the numbers shown:

126 APPENDIX D: OBTAINING SUPPORT FOR YOUR PRODUCT
Austria
Belgium
Denmark
Finland
France
Germany
Hungary
Ireland
Israel
Italy
0800 297 468
0800 71429
800 17309
0800 113153
0800 917959
0800 182 1502
06800 12813
1 800 553 117
1800 945 3794
800 879489
Luxembourg
Netherlands
Norway
Poland
Portugal
South Africa
Spain
Sweden
Switzerland
U.K.
800 23625
0800 0227788
800 11376
00800 4411 357
800 831416
0800 995 014
900 938 919
020 795 482
0800 553 072
0800 096 3266
You can also obtain support in this region using the following URL:
http://emea.3com.com/support/email.html
Latin America Telephone Technical Support and Repair
Antigua Barbuda
Argentina Local Number
Argentina
Argentina
Aruba
Bahamas
Barbados
Belize
Bermuda
Bolivia
Brazil Local Number
Brazil
British Virgin Islands
Cayman Islands
Chile
Columbia Local Number
Colombia
Costa Rica
Curacao
Dominica
Dominique
Equador
El Salvador
French Guiana
Grenada
AT&T +800 988 2112
54 11 5556 3200
0 810 444 3COM
810 44 32 66
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
55 11 5643 2700
800 133 266
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
57 1 592 5000
800 011 3266
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
Guadalupe
Guatemala
Guyana
Haiti
Honduras
Jamaica
Mexico Local Number
Mexico
Mexico
Monserrat
Nicaragua
Panama
Paraguay
Peru
Puerto Rico
Saba Anquila
St. Kitts Neives
St. Lucia
St. Vincent
Suriname
Trinidad and Tobago
Turks and Caycos
Uruguay - Montevideo
Venezuela
Virgin Islands
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
52 55 52 01 00 04
01 800 849CARE
01 800 849 2273
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
AT&T +800 998 2112
You can also obtain support in this region using the following:
Spanish speakers, enter the URL:
http://lat.3com.com/lat/support/form.html
Portuguese speakers, enter the URL:
http://lat.3com.com/br/support/form.html
English speakers in Latin America should send e-mail to:
lat_support_anc@3com.com
Country Telephone Number Country Telephone Number

Contact Us 127
US and Canada Telephone Technical Support and Repair
1 800 876 3266
Country Telephone Number Country Telephone Number
128 APPENDIX D: OBTAINING SUPPORT FOR YOUR PRODUCT
GLOSSARY
802.11b The IEEE specification for wireless Ethernet which allows speeds of up to
11 Mbps. The standard provides for 1, 2, 5.5 and 11 Mbps data rates.
The rates will switch automatically depending on range and environment.
802.11g The IEEE specification for wireless Ethernet which allows speeds of up to
54 Mbps. The standard provides for 6, 12, 24, 36, 48 and 54 Mbps data
rates. The rates will switch automatically depending on range and
environment.
10BASE-T The IEEE specification for 10 Mbps Ethernet over Category 3, 4 or 5
twisted pair cable.
100BASE-TX The IEEE specification for 100 Mbps Fast Ethernet over Category 5
twisted-pair cable.
Access Point An Access Point is a device through which wireless clients connect to
other wireless clients and which acts as a bridge between wireless clients
and a wired network, such as Ethernet. Wireless clients can be moved
anywhere within the coverage area of the access point and still connect
with each other. If connected to an Ethernet network, the access point
monitors Ethernet traffic and forwards appropriate Ethernet messages to
the wireless network, while also monitoring wireless client radio traffic
and forwarding wireless client messages to the Ethernet LAN.
Ad Hoc mode Ad Hoc mode is a configuration supported by most wireless clients. It is
used to connect a peer to peer network together without the use of an
access point. It offers lower performance than infrastructure mode, which
is the mode the router uses. (see also Infrastructure mode.)
130 GLOSSARY
Auto-negotiation Some devices in the range support auto-negotiation. Auto-negotiation is
where two devices sharing a link, automatically configure to use the best
common speed. The order of preference (best first) is: 100BASE-TX full
duplex, 100BASE-TX half duplex, 10BASE-T full duplex, and 10BASE-T
half duplex. Auto-negotiation is defined in the IEEE 802.3 standard for
Ethernet and is an operation that takes place in a few milliseconds.
Bandwidth The information capacity, measured in bits per second, that a channel can
transmit. The bandwidth of Ethernet is 10 Mbps, the bandwidth of Fast
Ethernet is 100 Mbps. The bandwidth for 802.11b wireless is 11Mbps.
Category 3 Cables One of five grades of Twisted Pair (TP) cabling defined by the EIA/TIA-586
standard. Category 3 is voice grade cable and can only be used in
Ethernet networks (10BASE-T) to transmit data at speeds of up to 10
Mbps.
Category 5 Cables One of five grades of Twisted Pair (TP) cabling defined by the EIA/TIA-586
standard. Category 5 can be used in Ethernet (10BASE-T) and Fast
Ethernet networks (100BASE-TX) and can transmit data up to speeds of
100 Mbps. Category 5 cabling is better to use for network cabling than
Category 3, because it supports both Ethernet (10 Mbps) and Fast
Ethernet (100 Mbps) speeds.
Channel Similar to any radio device, the Wireless Cable/DSL router allows you to
choose different radio channels in the wireless spectrum. A channel is a
particular frequency within the 2.4GHz spectrum within which the Router
operates.
Client The term used to described the desktop PC that is connected to your
network.
DHCP Dynamic Host Configuration Protocol. This protocol automatically assigns
an IP address for every computer on your network. Windows 95,
Windows 98 and Windows NT 4.0 contain software that assigns IP
addresses to workstations on a network. These assignments are made by
the DHCP server software that runs on Windows NT Server, and Windows
95 and Windows 98 will call the server to obtain the address. Windows
98 will allocate itself an address if no DHCP server can be found.
GLOSSARY 131
DNS Server Address DNS stands for Domain Name System, which allows Internet host
computers to have a domain name (such as 3com.com) and one or more
IP addresses (such as 192.34.45.8). A DNS server keeps a database of
host computers and their respective domain names and IP addresses, so
that when a domain name is requested (as in typing “3com.com” into
your Internet browser), the user is sent to the proper IP address. The DNS
server address used by the computers on your home network is the
location of the DNS server your ISP has assigned.
DSL modem DSL stands for digital subscriber line. A DSL modem uses your existing
phone lines to send and receive data at high speeds.
Encryption A method for providing a level of security to wireless data transmissions.
The Router uses two levels of encryption; 40/64 bit and 128 bit. 128 bit is
a more powerful level of encryption than 40/64 bit.
ESSID Extended Service Set Identifier. The ESSID is a unique identifier for your
wireless network. You must have the same ESSID entered into the router
and each of it's wireless clients.
Ethernet A LAN specification developed jointly by Xerox, Intel and Digital
Equipment Corporation. Ethernet networks use CSMA/CD to transmit
packets at a rate of 10 Mbps over a variety of cables.
Ethernet Address See MAC address.
Fast Ethernet An Ethernet system that is designed to operate at 100 Mbps.
Firewall Electronic protection that prevents anyone outside of your network from
seeing your files or damaging your computers.
Full Duplex A system that allows packets to be transmitted and received at the same
time and, in effect, doubles the potential throughput of a link.
Half Duplex A system that allows packets to transmitted and received, but not at the
same time. Contrast with full duplex.
132 GLOSSARY
Hub A device that regenerates LAN traffic so that the transmission distance of
that signal can be extended. Hubs are similar to repeaters, in that they
connect LANs of the same type; however they connect more LANs than a
repeater and are generally more sophisticated.
IEEE Institute of Electrical and Electronics Engineers. This American
organization was founded in 1963 and sets standards for computers and
communications.
IETF Internet Engineering Task Force. An organization responsible for
providing engineering solutions for TCP/IP networks. In the network
management area, this group is responsible for the development of the
SNMP protocol.
Infrastructure mode Infrastructure mode is the wireless configuration supported by the Router.
You will need to ensure all of your clients are set up to use infrastructure
mode in order for them to communicate with the Access Point built into
your Router. (see also Ad Hoc mode)
IP Internet Protocol. IP is a layer 3 network protocol that is the standard for
sending data through a network. IP is part of the TCP/IP set of protocols
that describe the routing of packets to addressed devices. An IP address
consists of 32 bits divided into two or three fields: a network number and
a host number or a network number, a subnet number, and a host
number.
IP Address Internet Protocol Address. A unique identifier for a device attached to a
network using TCP/IP. The address is written as four octets separated with
periods (full-stops), and is made up of a network section, an optional
subnet section and a host section.
IPsec IP Security. Provides IP network-layer encryption. IPSec can support large
encryption networks (such as the Internet) by using digital certificates for
device authentication. When setting up an IPSec connection between
two devices, make sure that they support the same encryption method.
ISP Internet Service Provider. An ISP is a business that provides connectivity to
the Internet for individuals and other businesses or organizations.
GLOSSARY 133
LAN Local Area Network. A network of end stations (such as PCs, printers,
servers) and network devices (hubs and switches) that cover a relatively
small geographic area (usually not larger than a floor or building). LANs
are characterized by high transmission speeds over short distances (up to
1000 metres).
MAC Media Access Control. A protocol specified by the IEEE for determining
which devices have access to a network at any one time.
MAC Address Media Access Control Address. Also called the hardware or physical
address. A layer 2 address associated with a particular network device.
Most devices that connect to a LAN have a MAC address assigned to
them as they are used to identify other devices in a network. MAC
addresses are 6 bytes long.
NAT Network Address Translation. NAT enables all the computers on your
network to share one IP address. The NAT capability of the Router allows
you to access the Internet from any computer on your home network
without having to purchase more IP addresses from your ISP.
Network A Network is a collection of computers and other computer equipment
that are connected for the purpose of exchanging information or sharing
resources. Networks vary in size, some are within a single room, others
span continents.
Network Interface
Card (NIC)
A circuit board installed into a piece of computing equipment, for
example, a computer, that enables you to connect it to the network. A
NIC is also known as an adapter or adapter card.
Protocol A set of rules for communication between devices on a network. The
rules dictate format, timing, sequencing and error control.
PPPoE Point-to-Point Protocol over Ethernet. Point-to-Point Protocol is a method
of data transmission originally created for dial-up connections; PPPoE is
for Ethernet connections.
PPTP Point-to-Point Tunneling Protocol is a method of secure data transmission
between two remote sites over the internet.
134 GLOSSARY
RJ-45 A standard connector used to connect Ethernet networks. The “RJ”
stands for “registered jack”.
Router A device that acts as a central hub by connecting to each computer's
network interface card and managing the data traffic between the local
network and the Internet.
Server A computer in a network that is shared by multiple end stations. Servers
provide end stations with access to shared network services such as
computer files and printer queues.
SSID Service Set Identifier. Some vendors of wireless products use SSID
interchangeably with ESSID.
Subnet Address An extension of the IP addressing scheme that allows a site to use a single
IP network address for multiple physical networks.
Subnet mask A subnet mask, which may be a part of the TCP/IP information provided
by your ISP, is a set of four numbers configured like an IP address. It is
used to create IP address numbers used only within a particular network
(as opposed to valid IP address numbers recognized by the Internet,
which must assigned by InterNIC).
Subnets A network that is a component of a larger network.
Switch A device that interconnects several LANs to form a single logical LAN that
comprises of several LAN segments. Switches are similar to bridges, in
that they connect LANs of a different type; however they connect more
LANs than a bridge and are generally more sophisticated.
TCP/IP Transmission Control Protocol/Internet Protocol. This is the name for two
of the most well-known protocols developed for the interconnection of
networks. Originally a UNIX standard, TCP/IP is now supported on almost
all platforms, and is the protocol of the Internet.
TCP relates to the content of the data travelling through a network —
ensuring that the information sent arrives in one piece when it reaches its
destination. IP relates to the address of the end station to which data is
being sent, as well as the address of the destination network.
GLOSSARY 135
Traffic The movement of data packets on a network.
universal plug and
play
Universal plug and play is a system which allows compatible applications
to read some of their settings from the Router. This allows them to
automatically configure some, or all, of their settings and need less user
configuration.
URL Filter A URL Filter is a feature of a firewall that allows it to stop its clients form
browsing inappropriate Web sites.
WAN Wide Area Network. A network that connects computers located in
geographically separate areas (for example, different buildings, cities, or
countries). The Internet is an example of a wide area network.
WDS Wireless Distribution System. WDS enables one or more Access Points to
rebroadcast received signals to extend range and reach, though this can
affect the overall throughput of data.
WECA Wireless Ethernet Compatibility Alliance. An industry group formed to
certify cross vendor interoperability and compatibility of 802.11b and
802.11g wireless networking products and to promote the standard for
enterprise, small business and home environments. (see also 802.11b,
802.11g, Wi-Fi)
WEP Wired Equivalent Privacy. A shared key encryption mechanism for wireless
networking. Encryption strength is 40/64 bit or 128 bit.
Wi-Fi Wireless Fidelity. This is the certification granted by WECA to products
that meet their interoperability criteria. (see also 802.11b, WECA)
Wireless Client The term used to describe a desktop or mobile PC that is wirelessly
connected to your wireless network.
Wireless LAN Service
Area
Another term for ESSID (Extended Service Set Identifier).
Wizard A Windows application that automates a procedure such as installation
or configuration.
136 GLOSSARY
WLAN Wireless Local Area Network. A WLAN is a group of computers and
devices connected together by wireless in a relatively small area (such as a
house or office).
WPA Wi-Fi Protected Access. A dynamically changing encryption mechanism
for wireless networking. Encryption strength is 256 bit.

137
REGULATORY NOTICES
FOR THE OFFICECONNECT ADSL WIRELESS 11G FIREWALL ROUTER
GENERAL STATEMENTS The 3Com OfficeConnect ADSL 11g Firewall Router, Model Number: WL-552 (3CRWDR100A-72,
3CRWDR100A-72, 3CRWDR100A-72) must be installed and used in strict accordance with the
manufacturer's instructions as described in the user documentation that comes with the product.
This product contains encryption. It is unlawful to export out of the U.S. without obtaining a U.S. Export
License.
This product does not contain any user serviceable components. Any unauthorized product changes or
modifications will invalidate 3Com's warranty and all applicable regulatory certifications and approvals.
EXPOSURE TO RADIO
FREQUENCY RADIATION
This device generates and radiates radio-frequency energy. In order to comply with FCC radio-frequency
exposure guidelines for an uncontrolled environment, this equipment must be installed and operated while
maintaining a minimum body to antenna distance of 20 cm (approximately 8 in).
The installer of this radio equipment must ensure that the antenna is located or pointed such that it does not
emit RF field in excess of Health Canada limits for the general population; consult Safety Code 6, obtainable
from Health Canada's website www.hc-sc.gc.ca/rpb.
This product must maintain a minimum body to antenna distance of 20 cm. Under these conditions this
product will meet the Basic Restriction limits of 1999/519/EC [Council Recommendation of 12 July 1999 on
the limitation of exposure of the general public to electromagnetic fields (0 Hz to 300 GHz)].
US - RADIO FREQUENCY
REQUIREMENTS
This device must not be co-located or operated in conjunction with any other antenna or transmitter.
US FEDERAL
COMMUNICATIONS
COMMISSION (FCC) EMC
COMPLIANCE
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates, uses and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may cause harmful interference to
radio communications. However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the interference by
one or more of the following measures:
■Reorient or relocate the receiving antenna.
■Increase the separation between the equipment and receiver.
■Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
■Consult the dealer or an experienced radio/TV technician for help.
The user may find the following booklet prepared by the Federal Communications Commission helpful:
The Interference Handbook
This booklet is available from the U.S. Government Printing Office, Washington, D.C. 20402. Stock No.
004-000-0034504.
3Com is not responsible for any radio or television interference caused by unauthorized modification of the
devices included with this 3Com OfficeConnect ADSL 11g Firewall Router, Model Number: WL-552
(3CRWDR100A-72, 3CRWDR100A-72, 3CRWDR100A-72), or the substitution or attachment of connecting
cables and equipment other than specified by 3Com.
The correction of interference caused by such unauthorized modification, substitution or attachment will be
the responsibility of the user.
Changes or modifications not expressly approved by 3Com could void the user's authority to operate this
equipment.
US MANUFACTURER'S FCC
DECLARATION OF
CONFORMITY
3Com Corporation
350 Campus Drive
Marlborough, MA 01752-3064, USA
(508) 323-5000
Date: July 19, 2005
Declares that the Product:
Brand Name: 3Com Corporation
Model Number: WL-552
Equipment Type: OfficeConnect ADSL 11g Firewall Router
138
Complies with Part 15 of the FCC rules. Operation is subject to the following two conditions: (1) this device
may not cause harmful interference, and (2) this device must accept any interference received, including
interference that may cause undesired operation.
INDUSTRY CANADA - RF
COMPLIANCE
This device complies with RSS 210 of Industry Canada.
Operation is subject to the following two conditions: (1) this device may not cause interference, and (2) this
device must accept any interference, including interference that may cause undesired operation of this
device.
L ` utilisation de ce dispositif est autorisee seulement aux conditions suivantes: (1) il ne doit pas produire de
brouillage et (2) l' utilisateur du dispositif doit etre pret a accepter tout brouillage radioelectrique recu, meme
si ce brouillage est susceptible de compromettre le fonctionnement du dispositif.
The term "IC" before the equipment certification number only signifies that the Industry Canada technical
specifications were met.
To reduce potential radio interference to other users, the antenna type and its gain should be so chosen that
the equivalent isotropically radiated power (EIRP) is not more than that required for successful
communication. To prevent radio interference to the licensed service, this device is intended to be operated
indoors and away from windows to provide maximum shielding. Equipment (or its transmit antenna) that is
installed outdoors is subject to licensing.
Pour empecher que cet appareil cause du brouillage au service faisant l'objet d'une licence, il doit etre utilize
a l'interieur et devrait etre place loin des fenetres afin de Fournier un ecram de blindage maximal. Si le matriel
(ou son antenne d'emission) est installe a l'exterieur, il doit faire l'objet d'une licence.
INDUSTRY CANADA -
EMISSIONS COMPLIANCE
STATEMENT
This Class B digital apparatus complies with Canadian ICES-003.
AVIS DE CONFORMITé à LA
RéGLEMENTATION
D'INDUSTRIE CANADA
Cet appareil numérique de la classe B est conform à la norme NMB-003 du Canada.
SAFETY COMPLIANCE NOTICE This device has been tested and certified according to the following safety standards and is intended for use
only in Information Technology Equipment which has been tested to these or other equivalent standards:
■UL Standard 60950 (3rd Edition) or 60950
■CAN/CSA C22.2 No. 60950 or 60950
■IEC 60950
■EN 60950
EU COMPLIANCE
3Com OfficeConnect ADSL 11g Firewall
Router
Model WL-552
For connection to ADSL networks
This equipment may be operated in:
AT BE CY CZ DK EE FI FR
DE GR HU IE IT LV LT LU
MT NL PL PT SK SI ES SE
GB IS LI NO CH BG RO TR

139
Intended use: ADSL 802.11g/b Firewall Router
For connection to ADSL networks
NOTE: To ensure product operation is in compliance with local regulations, select the country in which the
product is installed. Refer to 3CRWDR100A-72, 3CRWDR100A-72, 3CRWDR100A-72 User Guide.
A copy of the signed Declaration of Conformity can be downloaded from the Product Support web page for
the 3Com OfficeConnect ADSL 11g Firewall Router (3CRWDR100A-72, 3CRWDR100A-72,
3CRWDR100A-72) at http://www.3com.com.
English Hereby, 3Com Corporation, declares that this RLAN device is in compliance with
the essential requirements and other relevant provisions of Directive 1999/5/EC.
Finnish 3Com Corporation vakuuttaa täten että RLAN device tyyppinen laite on direktiivin
1999/5/EY oleellisten vaatimusten ja sitä koskevien direktiivin muiden ehtojen
mukainen.
Dutch Hierbij verklaart 3Com Corporation dat het toestel RLAN device in
overeenstemming is met de essentiële eisen en de andere relevante bepalingen van
richtlijn 1999/5/EG
Bij deze verklaart 3Com Corporation dat deze RLAN device voldoet aan de
essentiële eisen en aan de overige relevante bepalingen van Richtlijn 1999/5/EC.
French Par la présente 3Com Corporation déclare que l'appareil RLAN device est conforme
aux exigences essentielles et aux autres dispositions pertinentes de la directive
1999/5/CE
Par la présente, 3Com Corporation déclare que ce RLAN device est conforme aux
exigences essentielles et aux autres dispositions de la directive 1999/5/CE qui lui
sont applicables
Swedish Härmed intygar 3Com Corporation att denna RLAN device står I överensstämmelse
med de väsentliga egenskapskrav och övriga relevanta bestämmelser som framgår
av direktiv 1999/5/EG
German Hiermit erklärt 3Com Corporation, dass sich dieser/diese/dieses Managed Accces
Point in Übereinstimmung mit den grundlegenden Anforderungen und den
anderen relevanten Vorschriften der Richtlinie 1999/5/EG befindet". (BMWi)
Hiermit erklärt 3Com Corporation die Übereinstimmung des Gerätes RLAN device
mit den grundlegenden Anforderungen und den anderen relevanten Festlegungen
der Richtlinie 1999/5/EG. (Wien)
Greek ΜΕ ΤΗΝ ΠΑΡΟΥΣΑ 3Com Corporation ∆ΗΛΩΝΕΙ ΟΤΙ RLAN device
ΣΥΜΜΟΡΦΩΝΕΤΑΙ ΠΡΟΣ ΤΙΣ ΟΥΣΙΩ∆ΕΙΣ ΑΠΑΙΤΗΣΕΙΣ ΚΑΙ ΤΙΣ ΛΟΙΠΕΣ
ΣΧΕΤΙΚΕΣ ∆ΙΑΤΑΞΕΙΣ ΤΗΣ Ο∆ΗΓΙΑΣ 1999/5/ÅÊ
Italian Con la presente 3Com Corporation dichiara che questo RLAN device è conforme ai
requisiti essenziali ed alle altre disposizioni pertinenti stabilite dalla direttiva
1999/5/CE.
Spanish Por medio de la presente 3Com Corporation declara que el RLAN device cumple
con los requisitos esenciales y cualesquiera otras disposiciones aplicables o exigibles
de la Directiva 1999/5/CE
Portuguese 3Com Corporation declara que este RLAN device está conforme com os requisitos
essenciais e outras disposições da Directiva 1999/5/CE.
Malti Hawnhekk, 3Com Corporation, jiddikjara li dan RLAN device jikkonforma
mal-htigijiet essenzjali u ma provvedimenti orajn relevanti li hemm
fid-Dirrettiva 1999/5/EC
Estonian Käesolevaga kinnitab 3Com Corporation seadme RLAN device vastavust direktiivi
1999/5/EÜ põhinõuetele ja nimetatud direktiivist tulenevatele teistele asjakohastele
sätetele.
Hungarian Alulírott, 3Com Corporation nyilatkozom, hogy a RLAN device megfelel a
vonatkozó alapvetõ követelményeknek és az 1999/5/EC irányelv egyéb
elõírásainak.
Slovak 3Com Corporation týmto vyhlasuje, ze RLAN device spĺňa základné
po_iadavky a všetky príslušné ustanovenia Smernice 1999/5/ES.
Czech 3Com Corporation tímto prohlašuje, ze tento RLAN device je ve shodě se
základními pozadavky a dalšími příslušnými ustanoveními směrnice 1999/5/ES.
Slovene Šiuo 3Com Corporation deklaruoja, kad šis RLAN device atitinka esminius
reikalavimus ir kitas 1999/5/EB Direktyvos nuostatas.
Lithuanian Šiuo 3Com Corporation deklaruoja, kad šis RLAN device atitinka esminius
reikalavimus ir kitas 1999/5/EB Direktyvos nuostatas.
Latvian Ar šo 3Com Corporation deklarç, ka RLAN device atbilst Direktîvas 1999/5/EK
bûtiskajâm prasîbâm un citiem ar to saistîtajiem noteikumiem.

140
Also available at http://support.3com.com/doc/WL-552_EU_DOC.pdf
EU - RESTRICTIONS FOR USE
IN THE 2.4GHZ BAND
This device may be operated indoors or outdoors in all countries of the European Community using the
2.4GHz band: Channels 1 - 13, except where noted below.
■In Italy the end-user must apply for a license from the national spectrum authority to operate this device
outdoors.
■In Belgium outdoor operation is only permitted using the 2.46 - 2.4835 GHz band: Channel 13.
■In France outdoor operation is only permitted using the 2.4 - 2.454 GHz band: Channels 1 - 7.
BRAZIL RF COMPLIANCE Este equipamento opera em caráter secundário, isto é, não tem direito a proteção contra interferência
prejudicial, mesmo de estações do mesmo tipo, e não causar interferência a sistema operando em caráter
primário.

INDEX
Numbers
128-bit WEP 46
128-bit WEP Screen 46
1483 Bridge Mode 55
64-bit WEP Screen 47
A
Access Control Screen 62
Add PC Screen 63
Add Schedule Rule Screen 65
Addresses
IP 85
Admin Password Screen 75
ADSL Status Screen 77
Advanced Screen 68
Automatic Addressing 87
B
Backup/Restore Settings Screen 74
Bridge Mode for Single PC Screen 53
Bridged Mode Configuration Screen 33
C
Cable Specifications 91
Channels 111
Configuration Summary Screen 37
Connection Type Screen 29, 50
Conventions
notice icons, About This Guide 8
text, About This Guide 8
D
DDNS 70
DHCP 87
DHCP Clients List 42
DHCP server 25, 42
disabling 26
DMZ Screen 67
DNS 24
DNS Screen 55
DSL mode 29
Dynamic Domain Server (DDNS) Screen 70
Dynamic IP Address 34
Dynamic/Fixed IP for Bridge Mode Screen 35, 55
DYNDNS 70
E
Editing DHCP Clients List Screen 42
Encryption Screen 44
Encryption, disabling 45
F
Firewall Screen 59
Forgotten Password 80
H
Hostname
configuring 56
Hostname and MAC Address Screen 56
I
Internet
addresses 85
Internet Properties Screen 26
Internet Protocol (TCP/IP) Properties Screen 24
IP Address 41, 85
IPSEC 68
L
LAN Settings Screen 41
LED 14
LEDs 14
Local Area Properties Screen 24
Logs Screen 77
M
MAC Address 56

142 INDEX
configuring 56
MAC Address Filtering Screen 66
mode 30
N
NAT (Network Address Translation) 68
NAT-T (NAT Traversal) 68
Network
addresses 85
Networking
wireless 81
NICwireless 14
P
Password 27, 75
Poison Reverse 58
PPPoA 31
PPPoA Screen 31
PPPoA Settings Screen 52
PPPoE 26, 30, 31
PPPoE Screen 30
PPPoE Settings Screen 51
R
Remote Admin 68
Reset to Factory Default Screen 73
Reset to Factory Defaults 80
Restart Router Screen 73
RFC 1483 Bridged Mode 32, 53
RFC 1483 Routed Mode 34
RIP (Routing Information Protocol) 57
RIP Parameter Screen 58
Router Login Screen 28
Routing Mode Screen 34
Routing Table Screen 59
S
Schedule Rule Screen 65
Setup Wizard 27
SNMP Community Screen 71
SNMP Trap Screen 72
Special Applications Screen 60
Specifications
technical 89
SSID 31, 32, 33, 35, 36, 43
Static Addressing 87
Static Route Parameters Screen 57
Status Screen 28, 40
Subnet Mask 85
T
TCP/IP 23, 25, 85
Technical
specifications 89
standards 89
Time and Time Zone screen 76
TZO.com 70
U
Universal Plug and Play 68
Upgrade Screen 74
URL Blocking Screen 64
V
Virtual Servers Screen 61
VPI/VCI 30, 32, 33, 34, 36
W
WAN Ping Blocking 68
WDS 49
Web Browser Location Field 27
Web Proxy 26
WiFi Protected Access 45, 48
Wireless
networking 81
NIC 14
Wireless Configuration Screen 43
Wireless Settings Screen 31, 32, 33, 35, 36, 43
Wireless WDS Settings Screen 49
WPA (with RADIUS Server) Screen 48
WPA-PSK (no server) Screen 45