Intel 622ANXH Intel Centrino Wireless-N+WiMax 6250 User Manual revised manual iaw FCC RT
Intel Mobile Communications Intel Centrino Wireless-N+WiMax 6250 revised manual iaw FCC RT
Intel >
Contents
- 1. User Manual
- 2. revised manual iaw FCC RT
revised manual iaw FCC RT









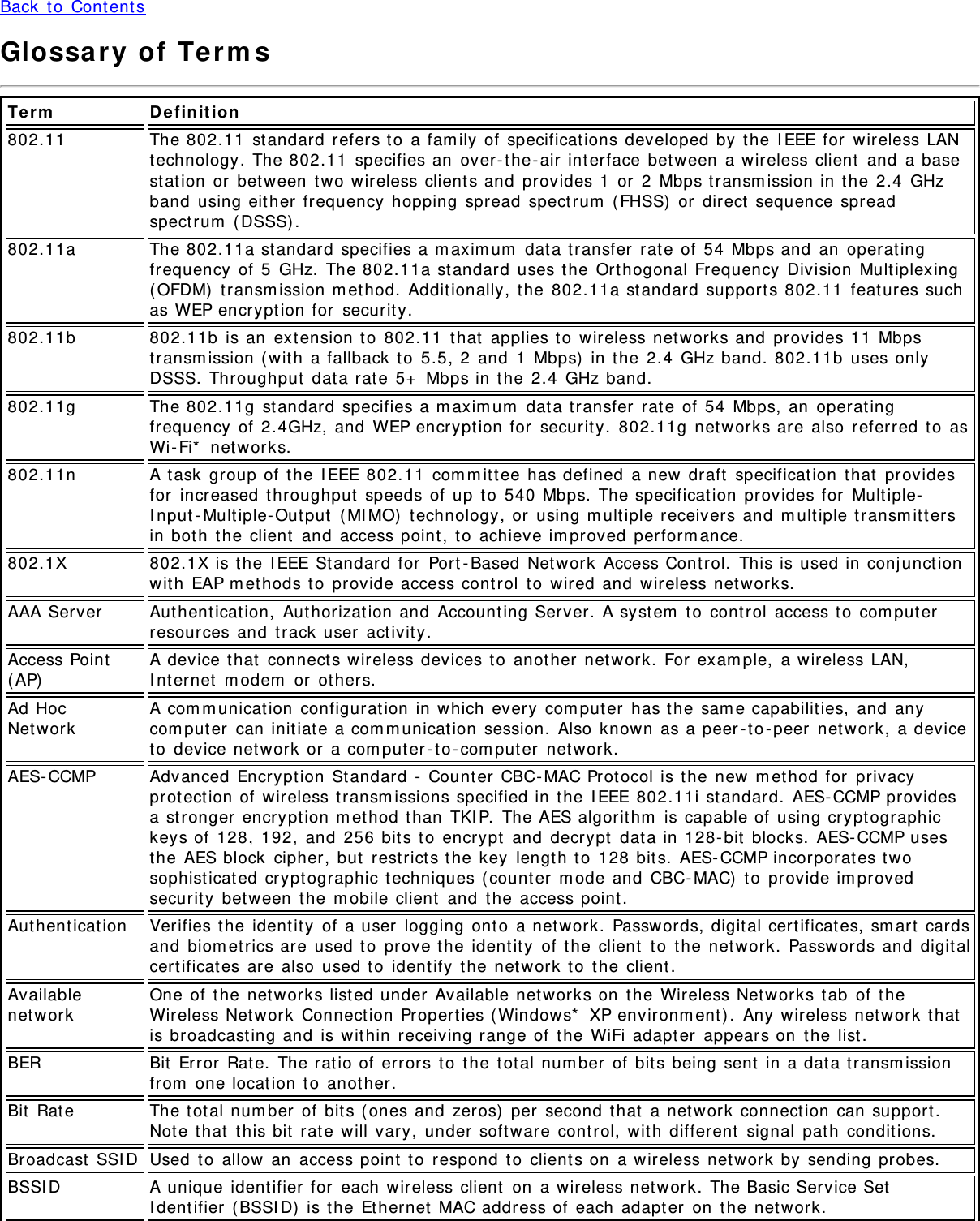
![This package is an SSL im plem ent ation written by Eric Young ( eay@crypt soft.com ) . The im plem ent at ion waswrit t en so as t o conform wit h Net scape's SSL.This library is free for com m ercial and non - com m ercial use as long as the following conditions are adhered t o. Thefollowing condit ions apply t o all code found in t his dist ribution, be it t he RC4, RSA, lhash, DES, et c., code; not j ustthe SSL code. The SSL docum entat ion included wit h this dist ribut ion is covered by t he sam e copyright term sexcept t hat t he holder is Tim Hudson ( t j h@crypt soft .com ).Copyright rem ains Eric Young's, and as such any Copyright not ices in t he code are not t o be rem oved. I f t hispackage is used in a product , Eric Young should be given attribut ion as t he aut hor of the parts of t he library used.This can be in t he form of a t ext ual m essage at program startup or in docum entat ion ( online or t ext ual) providedwit h the package.Redist ribution and use in source and binary form s, with or wit hout m odification, are perm it t ed provided t hat t hefollowing condit ions are m et :1. Redistribut ions of source code m ust ret ain t he copyright notice, t his list of condit ions and t he followingdisclaim er.2. Redistribut ions in binary form m ust reproduce t he above copyright not ice, t his list of condit ions and t hefollowing disclaim er in the docum entat ion and/ or ot her m at erials provided wit h the dist ribut ion.3. All advert ising m aterials m entioning feat ures or use of t his soft ware m ust display the followingacknowledgem ent : "This product includes crypt ographic soft ware written by Eric Young ( eay@crypt soft.com ) "The word 'crypt ographic' can be left out if t he rout ines from t he library being used are not crypt ographicrelat ed.4. I f you include any Windows specific code ( or a derivat ive t hereof) from t he apps directory ( applicat ion code)you m ust include an acknowledgem ent: "This product includes software writ t en by Tim Hudson( tj h@crypt soft .com ) "THI S SOFTWARE I S PROVI DED BY ERI C YOUNG "AS I S: ' AND ANY EXPRESS OR I MPLI ED WARRANTI ES,I NCLUDI NG, BUT NOT LI MI TED TO, THE I MPLI ED WARRANTI ES OF MERCHANTABI LI TY AND FI TNESS FOR APARTI CULAR PURPOSE ARE DI SCLAI MED. I N NO EVENT SHALL THE AUTHOR OR CONTRI BUTORS BE LI ABLE FORANY DI RECT, I NDI RECT, I NCI DENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTI AL DAMAGES ( I NCLUDI NG, BUTNOT LI MI TED TO, PROCUREMENT OF SUBSTI TUTE GOODS OR SERVI CES; LOSS OF USE, DATA, OR PROFI TS; ORBUSI NESS I NTERRUPTI ON) HOWEVER CAUSED AND ON ANY THEORY OF LI ABI LI TY, WHETHER I N CONTRACT,STRI CT LI ABI LI TY, OR TORT ( I NCLUDI NG NEGLI GENCE OR OTHERWI SE) ARI SI NG I N ANY WAY OUT OF THE USEOF THI S SOFTWARE, EVEN I F ADVI SED OF THE POSSI BI LI TY OF SUCH DAMAGE.The license and dist ribution t erm s for any publicly available version or derivat ive of t his code cannot be changed. i.e. t his code cannot sim ply be copied and put under another dist ribution license [ including t he GNU PublicLicense.]zlib.h - - inte rface of t he 'zlib' gene ral purpose com pression libra ry, ve rsion 1 .2 .3 , July1 8 t h, 2 0 0 5Copyright ( C) 1995 - 2005 Jean- loup Gailly and Mark AdlerThis soft ware is provided 'as- is', wit hout any express or im plied warrant y. I n no event will the aut hors be heldliable for any dam ages arising from t he use of t his soft ware. Perm ission is grant ed t o anyone t o use this soft warefor any purpose, including com m ercial applicat ions, and t o alter it and redist ribute it freely, subj ect t o t hefollowing restrict ions:1. The origin of t his software m ust not be m isrepresented; you m ust not claim that you wrote t he originalsoft ware. I f you use this soft ware in a product , an acknowledgm ent in t he product docum ent ation would beappreciat ed but is not required.2. Alt ered source versions m ust be plainly m arked as such, and m ust not be m isrepresent ed as being t heoriginal soft ware.3. This not ice m ay not be rem oved or alt ered from any source distribut ion.Jean - loup Gailly jloup@gzip.orgMark Adler m adler@alum ni.calt ech.edu](https://usermanual.wiki/Intel/622ANXH.revised-manual-iaw-FCC-RT/User-Guide-1637431-Page-29.png)



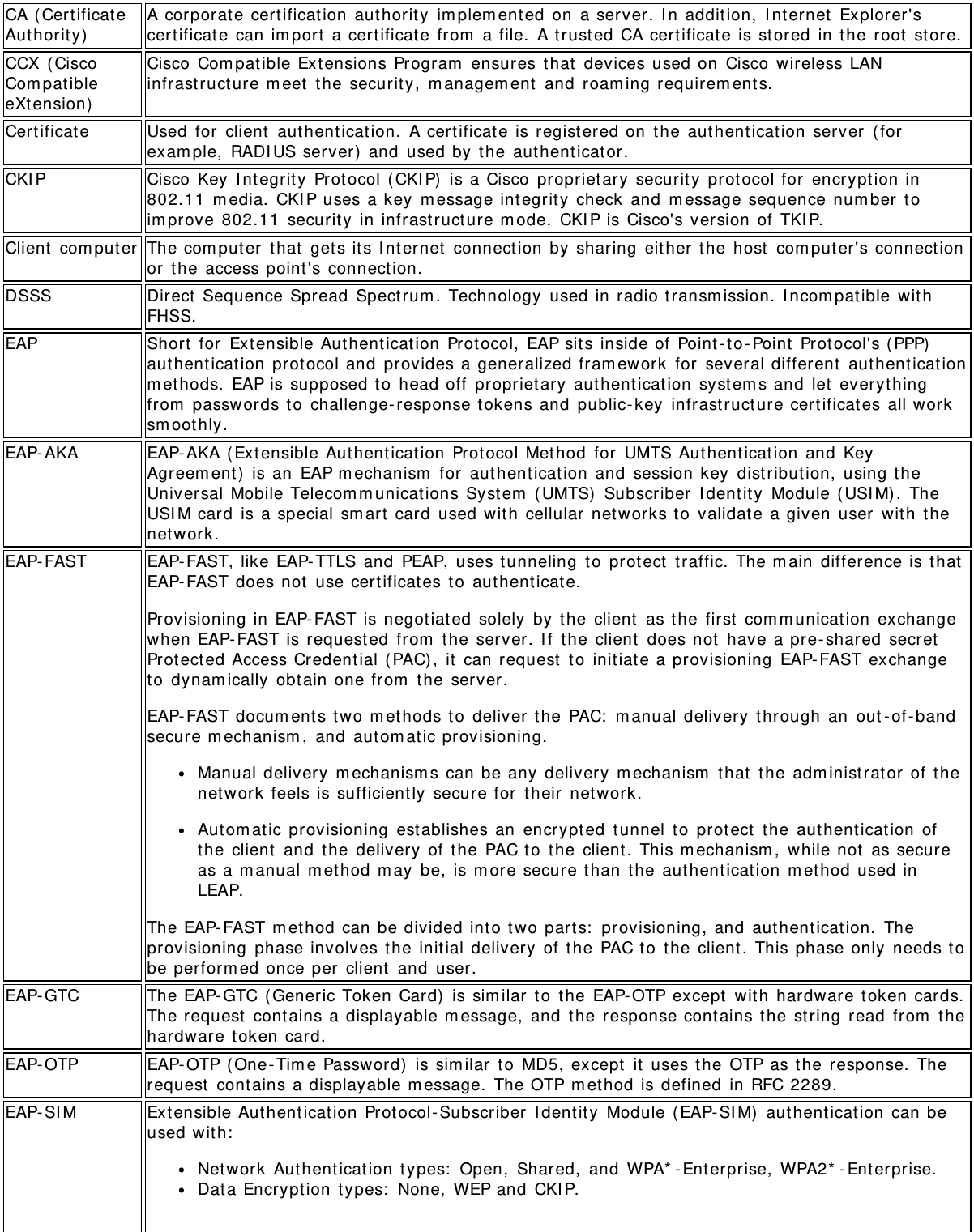
![Prot ocol) TKI P is part of the I EEE 802.11i encrypt ion st andard for wireless networks. TKI P is t he nextgenerat ion of WEP, t he Wired Equivalency Prot ocol, which is used t o secure 802.11 wirelessnet works. TKI P provides per packet key m ixing, a m essage integrit y check and a re- keyingm echanism , t hus fixing t he flaws of WEP.TLS (TransportLayer Securit y)A t ype of aut hent ication m et hod using the Ext ensible Aut hent ication Prot ocol ( EAP) and asecurit y prot ocol called t he Transport Layer Security ( TLS) . EAP- TLS uses cert ificat es which usepasswords. EAP- TLS authenticat ion supports dynam ic WEP key m anagem ent. The TLS prot ocol isint ended t o secure and authenticat e com m unicat ions across a public network through dat aencryption. The TLS Handshake Prot ocol allows t he server and client to provide m ut ualaut hent ication and t o negot iate an encrypt ion algorit hm and cryptographic keys before data ist ransm it ted.TTLS ( TunneledTransport LayerSecurit y)These set tings define t he prot ocol and t he credentials used to aut hent icate a user. I n TTLS, t heclient uses EAP- TLS t o validat e t he server and creat e a TLS-encrypted channel between t heclient and server. The client can use another authenticat ion prot ocol. Typically password- basedprot ocols challenge over t his encrypted channel to enable server validat ion. The challenge andresponse packets are sent over a non - exposed TLS encrypt ed channel. TTLS im plem ent ationstoday support all m et hods defined by EAP, as well as several older m et hods ( CHAP, PAP, MS-CHAP and MS- CHAP-V2) . TTLS can easily be ext ended to work wit h new prot ocols by definingnew attribut es to support new prot ocols.WEP ( WiredEquivalentPrivacy)Wired Equivalent Privacy, 64- and 128-bit ( 64 - bit is som et im es referred t o as 40 - bit) . This is alow -level encrypt ion t echnique designed to give the user about t he sam e am ount of privacy t hathe would expect from a LAN. WEP is a securit y prot ocol for wireless local area networks(WLANs) defined in t he 802.11b st andard. WEP is designed t o provide t he sam e level of securit yas t hat of a wired LAN. WEP aim s t o provide securit y by dat a over radio waves so that it isprot ect ed as it is t ransm it t ed from one end point t o anot her.WEP Key Either a pass phrase or hexadecim al key.The pass phrase m ust be 5 ASCI I charact ers for 64 - bit WEP or 13 ASCI I charact ers for 128-bitWEP. For pass phrases, 0 - 9, a- z, A- Z, and ~ ! @# $% ^ &* () _+ | ` - = { } | [ ] \ : "; '< > ?,./ are all validcharact ers.The hex key m ust be 10 hexadecim al characters ( 0 - 9, A- F) for 64 - bit WEP or 26 hexadecim alcharact ers ( 0 - 9, A- F) for 128- bit WEP.Wi - Fi*(WirelessFidelit y)I s m eant t o be used generically when referring of any t ype t o 802.11 net work, whether802.11b, 802.11a, or dual- band.WiMAX WiMAX, t he Worldwide I nt eroperability for Microwave Access, is a telecom m unicat ionstechnology aim ed at providing wireless data over long dist ances in a variet y of ways, from point -to - point links t o full m obile cellular type access. I t is based on t he I EEE 802.16 standard. Thenam e WiMAX was created by the WiMAX Forum , which was form ed in June 2001 t o prom oteconform ance and int eroperability of the st andard. The forum describes WiMAX as "a st andards-based t echnology enabling t he delivery of last m ile wireless broadband access as an alt ernativeto cable and DSL."Wireless rout er A st and - alone wireless hub t hat allows any com puter t hat has a wireless net work adapt er t ocom m unicate wit h anot her com put er wit hin t he sam e net work and t o connect to the I nt ernet.WLAN (WirelessLocal - AreaNet work)A t ype of local- area network that uses high - frequency radio waves rat her t han wires t ocom m unicate bet ween nodes.WPA* ( Wi- FiProt ect edAccess)This is a securit y enhancem ent t hat st rongly increases t he level of data prot ect ion and accesscont rol t o a wireless net work. WPA is an int erim st andard that will be replaced wit h t he I EEE's802.11i standard upon it s com plet ion. WPA consists of RC4 and TKI P and provides support forBSS ( I nfrast ruct ure) m ode only. WPA and WPA2 are com patible.WPA2* ( Wi- FiProt ect edAccess 2)This is the second generation of WPA t hat com plies wit h the I EEE TGi specification. WPA2consists of AES encrypt ion, pre-aut hent ication and PMKI D caching. I t provides support for BSS(I nfrastructure) m ode and I BSS ( ad hoc) m ode. WPA and WPA2 are com patible.WPA- Ent erprise Wi- Fi Prot ect ed Access- Ent erprise applies t o corporate users. A new standards- based,int eroperable securit y t echnology for wireless LAN ( subset of I EEE 802.11i draft st andard) thatencrypts data sent over radio waves. WPA is a Wi- Fi st andard t hat was designed t o im prove](https://usermanual.wiki/Intel/622ANXH.revised-manual-iaw-FCC-RT/User-Guide-1637431-Page-40.png)
