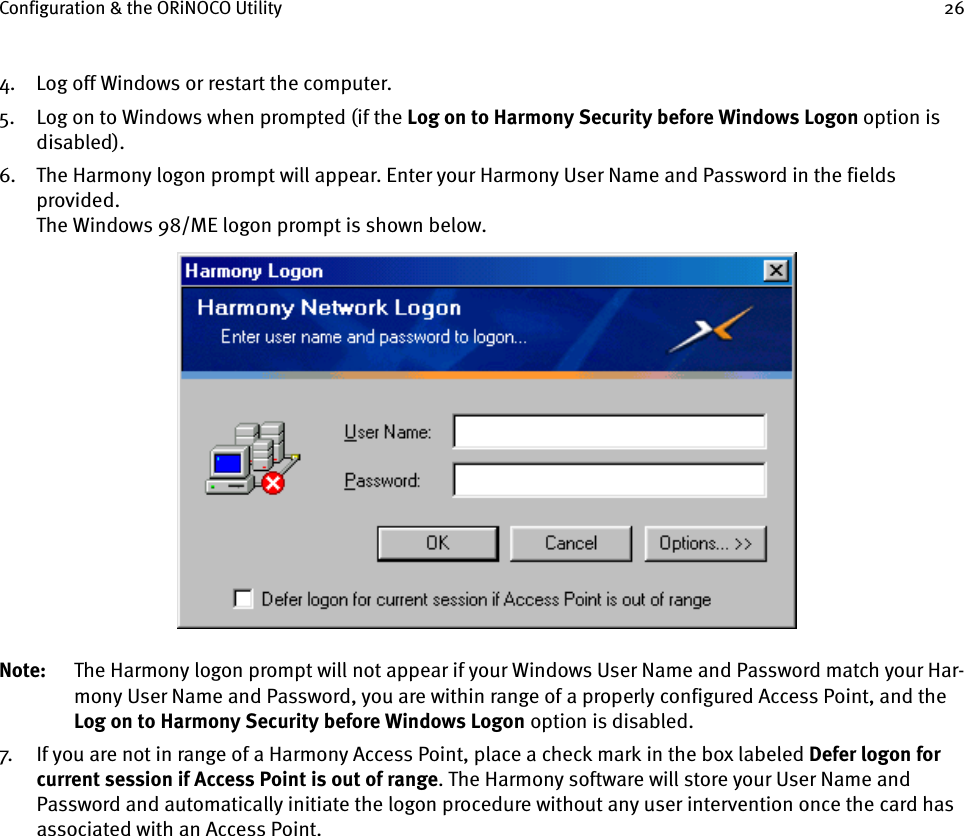
Proxim Wireless 8460 802.11a/b/g WIRELESS LAN CARDBUS CARD User Manual 11ab card
Proxim Wireless Corporation 802.11a/b/g WIRELESS LAN CARDBUS CARD 11ab card
Contents
- 1. MANUAL
- 2. CRN 23990 Revised User Manual
- 3. CRN 23989 Revised user manual
CRN 23990 Revised User Manual









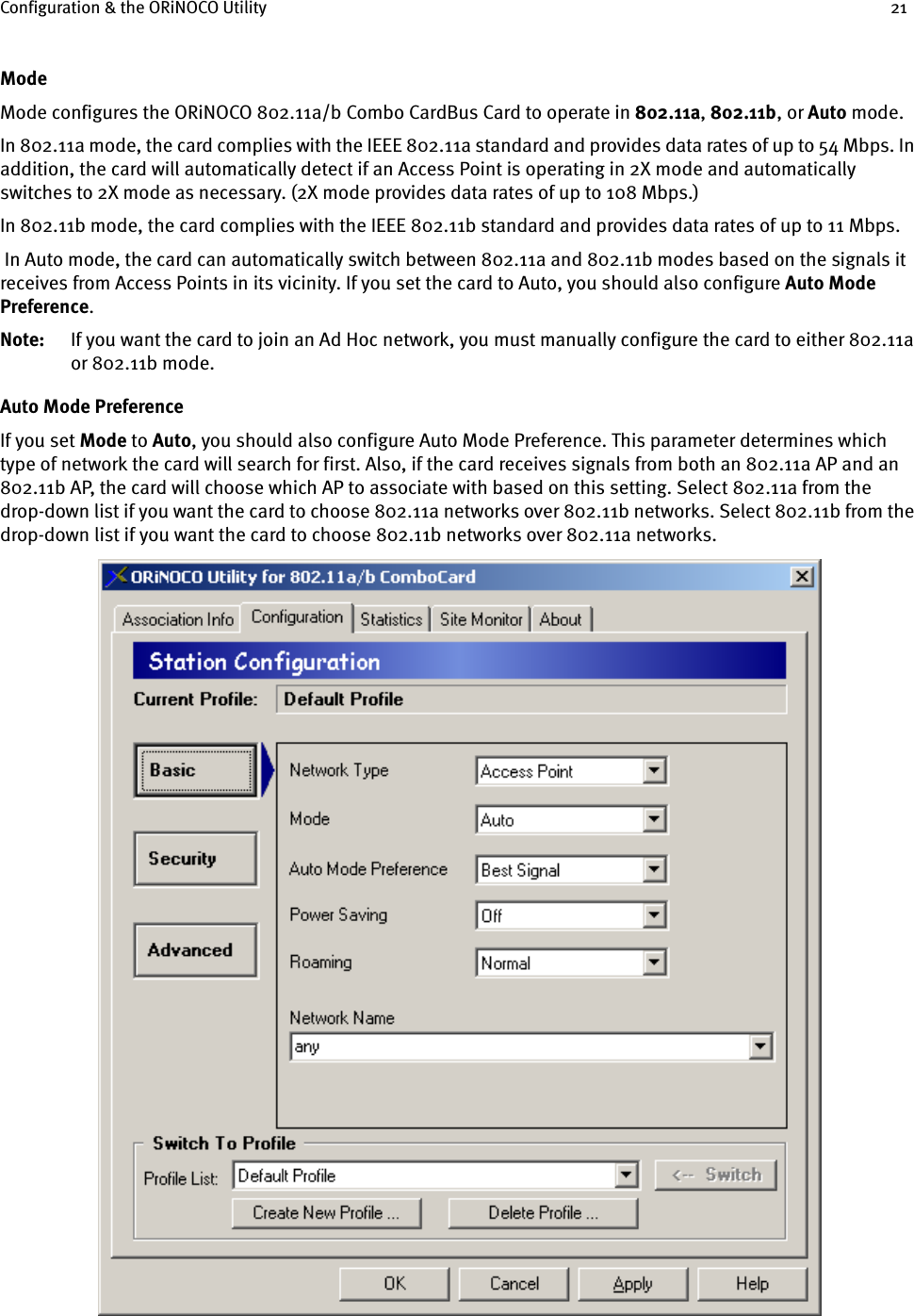

![Configuration & the ORiNOCO Utility 244. Enter one to four WEP Keys in the fields provided, as shown below.5. Use only hexadecimal digits (i.e., 0-9 and A-F). For 64-bit encryption, enter 10 digits for each Key; for 128-bit encryption, enter 26 digits for each Key; for 152-bit encryption, enter 32 digits for each Key.Note: If you created a text file that contains the WEP Keys, click Read Keys to upload those Keys to the card. See “Read Key File Format” on page 24 for formatting information.6. Click OK to save the WEP Keys.7. Select one of the Keys you configured as the Default Key.8. Click Apply or OK to save the new WEP settings.9. If you need to change a WEP Key at a later date, click Configure WEP Keys and enter one to four new WEP Keys. Note that any Keys you entered previously will not be visible (stars appear in place of the digits).Read Key File FormatIf you have multiple clients to configure, you can avoid having to enter each WEP Key manually by creating a text file that contains the Keys. Once you have the text file, you can upload the Keys to a client by clicking the Read Keys button found on the WEP Keys Configuration screen.To create the text file, use a text program such as Microsoft Notepad or WordPad. The text file should have a “.txt” extension. The first line of the text file must read “[WEP_KEY_VALUE]”. Then, enter one to four Keys in the following format: “key#=<key value>”, where # indicates the Key number (1-4) and <key value> is the specified Key’s hexadecimal digits. Each Key must be contain hexadecimal digits only (0-9 and A-F), and you must use the same number of digits for each Key. The number of digits depends upon the Key Size you select in the WEP Keys Configuration screen:• For 64 Bit, use 10 digits per Key.• For 128 Bit, use 26 digits per Key.• For 152 Bit, use 32 digits per Key.](https://usermanual.wiki/Proxim-Wireless/8460.CRN-23990-Revised-User-Manual/User-Guide-276371-Page-24.png)
![Configuration & the ORiNOCO Utility 25The following example illustrates the WEP Key file format for 64-bit encryption:[WEP_KEY_VALUE]key1=1234567890key2=0987654321key3=ABCDEF1234key4=ABCDEFABCDHarmony Security ProtocolThe Harmony Security Protocol automates encryption management, assigning a unique and dynamic WEP Key to each user. The Harmony Security Protocol includes the following features:•Uses 152-Bit WEP Encryption•Generates a unique WEP Key for each user that is valid only for the current network session•Periodically renews the user’s Harmony session and assigns a new WEP Key without requiring any end user interaction•Incorporates the end user’s logon prompt into Microsoft Windows’ standard logon procedure on the client deviceEach Harmony device plays a role in the Harmony Security Protocol: the AP Controllers maintain a database of user name and passwords to authenticate users; the Access Points block all network traffic to or from a client until after the user has been successfully authenticated by the Harmony System; and the Harmony client adapters include a software utility that incorporates the Harmony logon prompt into the standard Windows logon procedure.When the Harmony Security Protocol is enabled on a client adapter, the user is prompted to enter his or her Harmony User Name and Password during boot up, either immediately before or after the Windows logon prompt (depending on the device configuration).Once the user has been authenticated by the Harmony System, the wireless client receives a unique 152-bit WEP Key from the Harmony System, and it can begin to exchange data with the Ethernet network. Refer to the Harmony Access Point Controller User’s Guide for more information on the Harmony Security Protocol.Harmony Security Protocol Guidelines•If you want to use the Harmony Security Protocol on your network, you must enable the protocol on all of your network’s Harmony Access Points and clients.•At this time, the Harmony Security Protocol’s client application supports Windows 98 SE, ME, 2000 Profes-sional, and XP. The protocol does not support Windows 2000 Server or NT 4.0. •The Harmony Security Protocol is only available for clients that are operating in Infrastructure mode.•A network administrator who manages the network’s Harmony Access Point Controller(s) must assign each user a Harmony User Name and Password and enter this information into the Harmony System’s User Data-base. Refer to the Harmony Access Point Controller User’s Guide for details.•If you enable the Harmony Security Protocol, you do not need to configure WEP Keys on a wireless client (the Harmony System will generate keys for you). Follow these steps to enable the Harmony Security Protocol:1. Select Use Harmony Security Protocol within the Security Level box.2. Place a check mark in the Log on to Harmony Security before Windows Logon box if you want to connect to the wireless network before logging on to the Windows operating system.Note: You should enable the Log on to Harmony Security before Windows Logon option if your computer con-nects to a Windows Domain Controller, connects to a Novell network, automatically reconnects to shared network drives during Windows logon, or runs networking software (e.g., PC Anywhere) before connecting to the network.3. Click Apply or OK to save the new security settings.](https://usermanual.wiki/Proxim-Wireless/8460.CRN-23990-Revised-User-Manual/User-Guide-276371-Page-25.png)